Cabinetdetherapies collects 49 authentic Cisco CCNP Security 300-208 Exam questions and Answers, and 300-208 pdf online sharing downloads, we help you improve your skills if you want to pass Cisco 300-208 Exams need to be noted:
(Duration minutes (55-65 questions)), (available Languages English, Japanese), Exam Policies. It is recommended(but not required), that students have the following knowledge and skills before attending this course:
- Knowledge of Microsoft Windows operating system
- A CCNA Security certification
if you want to get “Implementing Cisco Secure Access Solutions (Sisas) v1.0 “is the 300-208 exam dump, CISCO 300-208 exam certification.
Cabinetdetherapies recommends that you: https://www.pass4itsure.com/300-208.html (q&as:356 PDF + VCE) is frequently updated and reviewed to pass the exam quickly.
[PDF]Free Cisco CCNP Security 300-208 dumps download from Google Drive: https://drive.google.com/open?id=1bnx5KvgWc2pqM6abxmK1Uephb9tHjAHi
[PDF]Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1Qzc3W-UXHXeCJZQZIsYAVUuIacAB5JWN
300-208 SISAS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/specialist-sisas.html
Free 49 Cisco CCNP Security 300-208 Practice test questions and answers
QUESTION 1
A network administrator is seeing a posture status “unknown” for a single corporate machine on the Cisco ISE authentication report, whereas the other machines are reported as “compliant”. Which option is the reason for machine being
reported as “unknown”?
A. Posture agent is not installed on the machine.
B. Posture policy does not support the OS.
C. Posfure compliance condition is missing on the machine.
D. Posture service is disabled on Cisco ISE.
Correct Answer: A
Explanation
QUESTION 2
Where is client traffic decrypted in a controller-based wireless network protected with WPA2 Security?
A. Access Point
B. Switch
C. Wireless LAN Controller
D. Authentication Server
Correct Answer: A
Explanation
QUESTION 3
Which two switchport commands enable MAB and allow non-802.1X capable devices to immediately run through the MAB process? (Choose two.)
A. authentication order mab dot1x
B. authentication order dot1x mab
C. no authentication timer
D. dot1x timeout tx-period
E. authentication open
F. mab
Correct Answer: AF
Explanation
QUESTION 4
Which three remediation actions are supported by the Web Agent for Windows? (Choose three.)
A. Automatic Remediation
B. Message text
C. URL Link
D. File Distribution
E. AV definition update
F. Launch Program
Correct Answer: BCD
Explanation
QUESTION 5
When using CA for identity source, which method can be used to provide real-time certificate validation?
A. X.509
B. PKI
C. OCSP
D. CRL
Correct Answer: D
Explanation
QUESTION 6
Which configuration must you perform on a switch to deploy Cisco ISE in low-impact mode?
A. Configure an ingress port ACL on the switchport.
B. Configure DHCP snooping globally.
C. Configure IP-device tracking.
D. Configure BPDU filtering.
Correct Answer: A
Explanation
QUESTION 7
Which command configures console port authorization under line con 0?
A. authorization default|WORD
B. authorization exec line con 0|WORD
C. authorization line con 0|WORD
D. authorization exec default|WORD
Correct Answer: D
Explanation
QUESTION 8
A security engineer has a new TrustSec project and must create a few static security group tag classifications as a proof of concept. Which two classifications can the tags be mapped to? (Choose two.)
A. VLAN
B. user ID
C. interface
D. switch ID
E. MAC address
Correct Answer: AC
Explanation
Explanation/Reference:
Explanation: In static classification the tag maps to some thing (an IP, subnet, VLAN, or interface) rather than relying on an authorization from the Cisco ISE.
This process of assigning the SGT is defined as “classification.” These classifications are thentransported deeper into the network for policy enforcement
QUESTION 9
Which description of the use of low-impact mode in a Cisco ISE deployment is correct?
A. It continues to use the authentication open capabilities of the switch port, which allows traffic to enter the switch before an authentication result.
B. Low-impact mode must be the final phase in deploying Cisco ISE into a network environment using the phased approach.
C. The port does not allow any traffic before the authentication (except for EAP, Cisco Discovery Protocol, and LLDP), and then the port is assigned to specific authorization results after the authentication.
D. It enables authentication (with authentication open), sees exactly which devices fail and which succeed, and corrects the failed authentications before they cause any problems.
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 10
When you select Centralized Web Auth in the ISE Authorization Profile, which two components host the web authentication portal? (Choose two.)
A. ISE
B. the WLCC. the access point
D. the switch
E. the endpoints
Correct Answer: BD
Explanation
QUESTION 11
Which definition of “posturing” as it relates to a general network infrastructure and access into the internal network is true?
A. The process by which an operating system or application running on an endpoint provides critical information about internet activity being used by the endpoint.
B. The process by which an endpoint device can be monitored while connected to the network to determine if it could contain viruses or potential harmful programs running.
C. The process by which an operating system or application running on an endpoint provides critical information about the software that is actively running on the device.
D. The process when software is uploaded to an end device before it is allowed to gain access to a secure network.
Correct Answer: D
Explanation
QUESTION 12
Which 2 options are functional components of the posture service?
A. Quarantined policy
B. Posture policy
C. Client provisioning
D. Network provisioning
Correct Answer: BC
Explanation
QUESTION 13
Which components must be selected for a client provisioning policy to do a Posture check on the Cisco ISE?
A. Configuration Wizard, Wizard Profile
B. Remediation Actions, Posture Requirements
C. Operating System, Posture Requirements
D. Agent, Profile, Compliance Module
Correct Answer: D
Explanation
QUESTION 14
Which two options can a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two.)
A. Known
B. Random
C. Monthly
D. Imported
E. Daily
F. Yearly
Correct Answer: BD
Explanation
QUESTION 15
Which advanced authentication setting is needed to allow an unknown device to utilize Central WebAuth?
A. If Authentication failed > Continue
B. If Authentication failed > Drop
C. If user not found > Continue
D. If user not found > Reject
Correct Answer: C
Explanation
QUESTION 16
Which three network access devices allow for static security group tag assignment? (Choose three.)
A. intrusion prevention system
B. access layer switch
C. data center access switch
D. load balancer
E. VPN concentrator
F. wireless LAN controller
Correct Answer: BCE
Explanation
QUESTION 17
Which three statements describe differences between TACACS+ and RADIUS? (Choose three.)
A. RADIUS encrypts the entire packet, while TACACS+ encrypts only the password.
B. TACACS+ encrypts the entire packet, while RADIUS encrypts only the password.
C. RADIUS uses TCP, while TACACS+ uses UDP.
D. TACACS+ uses TCP, while RADIUS uses UDP.
E. RADIUS uses ports 1812 and 1813, while TACACS+ uses port 49.
F. TACACS+ uses ports 1812 and 1813, while RADIUS uses port 49
Correct Answer: BDE
Explanation
QUESTION 18
Which protocol is EAP encapsulated in for communications between the authenticator and the authentication server ?
A. EAP-MD5
B. IPSec
C. EAPOL
D. Radius
Correct Answer: D
Explanation
QUESTION 19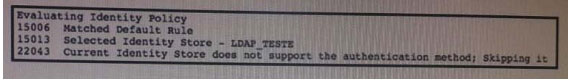 Refer to the exhibit. Which authentication method is being used?
Refer to the exhibit. Which authentication method is being used?
A. PEAP-MSCHAP
B. EAP-GTC
C. EAP-TLS
D. PEAP-TLSCorrect Answer: A
Explanation
Explanation/Reference:
These authentication methods are supported with LDAP:
Extensible Authentication Protocol
Generic Token Card (EAP-GTC) Extensible Authentication Protocol
Transport Layer Security (EAP-TLS) Protected Extensible Authentication Protocol
Transport Layer Security (PEAP-)
QUESTION 20
When MAB is configured, how often are ports reauthenticated by default?
A. every 60 seconds
B. every 90 seconds
C. every 120 seconds
D. never
Correct Answer: D
Explanation
QUESTION 21
You discover that the Cisco ISE is failing to connect to the Active Directory server. Which option is a possible cause of the problem?
A. NTP server time synchronization is configured incorrectly.
B. There is a certificate mismatch between Cisco ISE and Active Directory.
C. NAT statements required for Active Directory are configured incorrectly.
D. The RADIUS authentication ports are being blocked by the firewall.
Correct Answer: A
Explanation
QUESTION 22
Which feature must you configure on a switch to allow it to redirect wired endpoints to Cisco ISE?
A. the http secure-server command
B. RADIUS Attribute 29
C. the RADIUS VSA for accounting
D. the RADIUS VSA for URL-REDIRECT
Correct Answer: A
Explanation
QUESTION 23
Which debug command on a Cisco WLC shows the reason that a client session was terminated?
A. debug dot11 state enable
B. debug dot1x packet enable
C. debug client mac addr
D. debug dtls event enable
E. debug ap enable cisco ap
Correct Answer: C
Explanation
QUESTION 24
Which technology performs CoA support Posture Service?
A. External root CA
B. Cisco ACS
C. Cisco ISE
D. Internal root CA
Correct Answer: C
Explanation
QUESTION 25
Which supplicants(s) and server(s) are capable of supporting EAP-CHAINING?
A. Cisco AnyConnect NAM and Cisco Access Control Server
B. Cisco Secure Services Client and Cisco Access Control Server
C. Cisco AnyConnect NAM and Cisco Identity Service Engine
D. Windows Native Supplicant and Cisco Identity Service Engine
Correct Answer: C
Explanation
QUESTION 26
Which three algorithms should be avoided due to security concerns? (Choose three.)
A. DES for encryption
B. SHA-1 for hashing
C. 1024-bit RSA
D. AES GCM mode for encryption
E. HMAC-SHA-1
F. 256-bit Elliptic Curve Diffie-Hellman
G. 2048-bit Diffie-Hellman
Correct Answer: ABC
Explanation
QUESTION 27
Refer to the exhibit.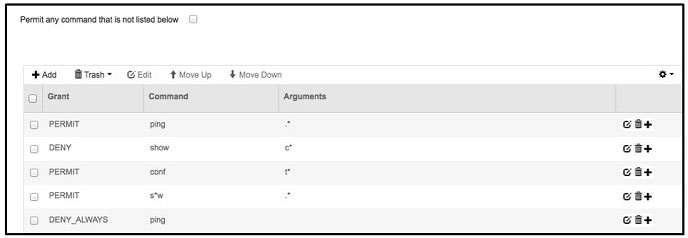 If a user with privilege 15 is matching this command set on Cisco ISE 2.0, which three commands can the user execute? (Choose three.)
If a user with privilege 15 is matching this command set on Cisco ISE 2.0, which three commands can the user execute? (Choose three.)
A. configure terminalB. show run
C. show clock
D. ping 10.10.100.1
E. exit
F. show ip interface brief
Correct Answer: ABF
Explanation
QUESTION 28
Which RADIUS attribute is used primarily to differentiate an IEEE 802.1x request from a Cisco MAB request?
A. RADIUS Attribute (5) NAS-Port
B. RADIUS Attribute (6) Service-Type
C. RADIUS Attribute (7) Framed-Protocol
D. RADIUS Attribute (61) NAS-Port-Type
Correct Answer: B
Explanation
QUESTION 29
What is a requirement for posture administration services in Cisco ISE?
A. at least one Cisco router to store Cisco ISE profiling policies
B. Cisco NAC Agents that communicate with the Cisco ISE server
C. an ACL that points traffic to the Cisco ISE deployment
D. the advanced license package must be installed
Correct Answer: D
Explanation
QUESTION 30
What attribute could be obtained from the SNMP query probe?
A. FQDN
B. CDP
C. DHCP class identifier
D. User agent
Correct Answer: B
Explanation
QUESTION 31
When using a DHCP probe in a Cisco ISE deployment, which type of request triggers an endpoint to be reprofiled?
A. DHCP Inform
B. REBINDING
C. RENEWING
D. INIT-REBOOT
Correct Answer: D
Explanation
QUESTION 32
Which two attributes must match between two Cisco ASA devices to properly enable high availability? (Choose two.)
A. model, interface configuration, and RAM
B. major and minor software release
C. tcp dead-peer detection protocol
D. 802.1x authentication identity
Correct Answer: AB
Explanation
QUESTION 33
Refer to Following:
aaa new model
tacacs-server host 1.1.1.1 single connection
tacas-server key cisco123
Which statement about the authentication protocol used in the configuration is true?
A. Authentication request contains username, encrypted password, NAS IP address, and port.
B. Authentication and authorization requests are sent in a single open connection between the network device and the TACACS+ server
C. Authentication request contains username, password, NAS IP address and port.
D. Authentication and authorization request packets are grouped together in a single packet.
Correct Answer: B
Explanation
QUESTION 34
Which three events immediately occur when a user clicks “Register” on their device in a single-SSID BYOD onboarding registration process (Choose three).
A. CA certificate is sent to the device from Cisco ISE
B. An endpoint is added to a RegistereDevices identity group
C. RADIUS access request is sent to Cisco ISE
D. The profile service is sent to the device from Cisco ISE
E. dACL is sent to the device from Cisco ISE
F. BYOD registration flag is set by Cisco ISE
Correct Answer: ABF
Explanation
QUESTION 35
Which two options can be pushed from Cisco ISE server as part of successful 802.1x authentication?
A. Reauthentication timer
B. DACL
C. Vlan
D. Authentication order
E. Posture status
F. Authentication priority
Correct Answer: BC
Explanation
QUESTION 36
A network administration wants to set up a posture condition on Cisco ISE to check for the file name Posture.txt in C:\ on a Windows machine. Which condition must the network administrator configuration?
A. Service condition
B. Registry condition
C. Application condition
D. File conditionCorrect Answer: D
Explanation
QUESTION 37
Which option is the code field of n EAP packet?
A. one byte and 1=request, 2=response 3=failure 4=success
B. two byte and 1=request, 2=response, 3=success, 4=failure
C. two byte and 1=request 2=response 3=failure 4=success
D. one byte and 1=request 2=response 3=success 4=failure
Correct Answer: D
Explanation
QUESTION 38
Which three components comprise the Cisco ISE profiler? (Choose three.)
A. the sensor, which contains one or more probes
B. the probe manager
C. a monitoring tool that connects to the Cisco ISE
D. the trigger, which activates ACLs
E. an analyzer, which uses configured policies to evaluate endpoints
F. a remitter tool, which fails over to redundant profilers
Correct Answer: ABE
Explanation
QUESTION 39
Which two Active Directory authentication methods are supported by Cisco ISE? (Choose two.)
A. MS-CHAPv2
B. PEAP
C. PPTP
D. EAP-PEAP
E. PPP
Correct Answer: AB
Explanation
QUESTION 40
What implementation must be added to the WLC to enable 802.1X and CoA for wireless endpoints?
A. the ISE
B. an ACL
C. a router
D. a policy server
Correct Answer: A
Explanation
QUESTION 41
Which two Cisco ISE administration options are available in the Default Posture Status setting? (Choose two.)
A. Unknown
B. Compliant
C. FailOpen
D. FailClose
E. Noncompliant
Correct Answer: BE
Explanation
QUESTION 42
Your guest-access wireless network is experiencing degraded performance and excessive latency due to user saturation. Which type of rate limiting can you implement on your network to correct the problem?
A. per-device
B. per-policy
C. per-access point
D. per-controller
E. per-application
Correct Answer: A
Explanation
QUESTION 43
Which network access device feature can you configure to gather raw endpoint data?
A. Device Sensor
B. Device Classifier
C. Switched Port Analyzer
D. Trust Anchor
Correct Answer: A
Explanation
QUESTION 44
Refer to the exhibit.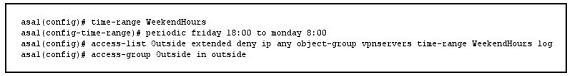 If the given configuration is applied to the object-group vpnservers, during which time period are external users able to connect?
If the given configuration is applied to the object-group vpnservers, during which time period are external users able to connect?
A. From Friday at 6:00 p.m. until Monday at 8:00 a.m.
B. From Monday at 8:00 a.m. until Friday at 6:00 p.m.
C. From Friday at 6:01 p.m. until Monday at 8:01 a.m.
D. From Monday at 8:01 a.m. until Friday at 5:59 p.m.
Correct Answer: A
Explanation
QUESTION 45
What are the initial steps to configure an ACS as a TACACS server?
A. 1. Choose Network Devices and AAA Clients > Network Resources.
2. Click Create.
B. 1. Choose Network Resources > Network Devices and AAA Clients.
2. Click Create.
C. 1. Choose Network Resources > Network Devices and AAA Clients.
2. Click Manage.
D. 1. Choose Network Devices and AAA Clients > Network Resources.
2. Click Install.Correct Answer: B
Explanation
Explanation/Reference:
QUESTION 46
Which statement about Cisco Management Frame Protection is true?
A. It enables stations to remain in power-save mode, except at specified intervals to receive data from the access point.
B. It detects spoofed MAC addresses.
C. It identifies potential RF jamming attacks.
D. It protects against frame and device spoofing.
Correct Answer: D
Explanation
QUESTION 47
CORRECT TEXT
The Secure-X company has recently successfully tested the 802.1X authentication deployment using the Cisco Catalyst switch and the Cisco ISEv1.2 appliance. Currently, each employee desktop is connected to an 802.1X enabled switch
port and is able to use the Cisco AnyConnect NAM 802.1Xsupplicantto log in and connect to the network.
Currently, a new testing requirement is to add a network printer to the Fa0/19 switch port and have it connect to the network. The network printer does not support 802.1X supplicant. The Fa0/19 switch port is now configured to use 802.1X
authentication only.
To support this network printer, the Fa0/19 switch port configuration needs to be edited to enable the network printer to authenticate using its MAC address. The network printer should also be on VLAN 9.
Another network security engineer responsible for managing the Cisco ISE has already per-configured all the requirements on the Cisco ISE, including adding the network printer MAC address to the Cisco ISE endpoint database and etc…
Your task in the simulation is to access the Cisco Catalyst Switch console then use the CLI
to:
Enable only the Cisco Catalyst Switch Fa0/19 switch port to authenticate the network printer using its MAC address and:
Ensure that MAC address authentication processing is not delayed until 802.1Xfails
Ensure that even if MAC address authentication passes, the switch will still perform 802.1X authentication if requested by a 802.1X supplicant
Use the required show command to verify the MAC address authentication on the Fa0/19 is successful
The switch enable password is Cisco
For the purpose of the simulation, to test the network printer, assume the network printer will be unplugged then plugged back into the Fa0/19 switch port after you have finished the required configurations on the Fa0/19 switch port.
Note: For this simulation, you will not need and do not have access to the ISE GUI To access the switch CLI, click the Switch icon in the topology diagram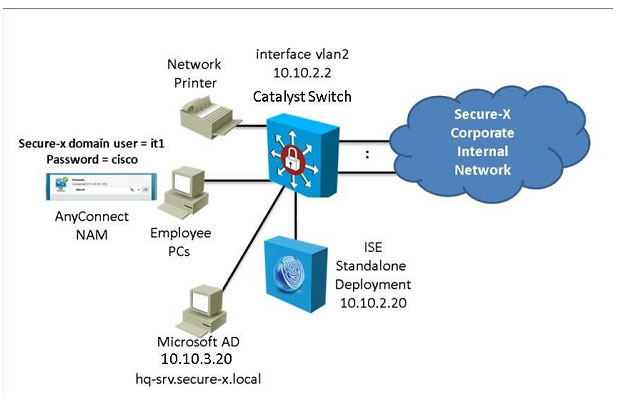 Correct Answer: Review the explanation for full configuration and solution.
Correct Answer: Review the explanation for full configuration and solution.
Explanation
Explanation/Reference:
Initial configuration for fa 0/19 that is already done: 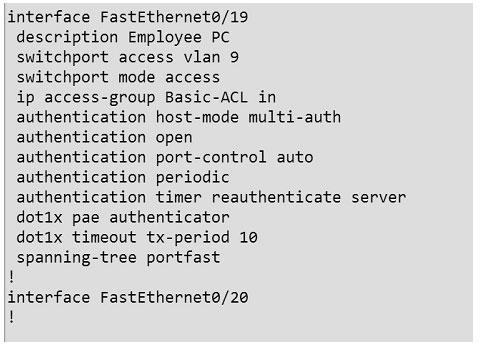
AAA configuration has already been done for us. We need to configure mac address bypass on this port to achieve the goal stated in the question. To do this we simply need to add this command under the interface:
mab
Then do a shut/no shut on the interface.
Verification: 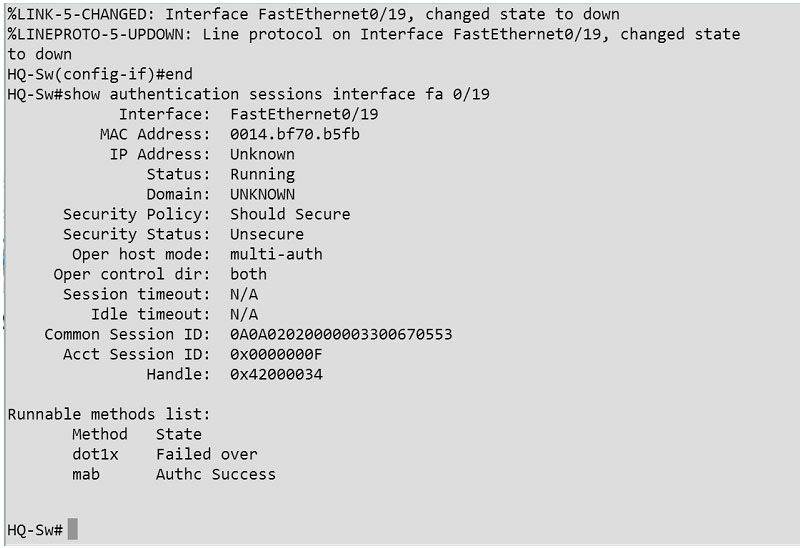
QUESTION 48
DRAG DROP
A security engineer is deploying Cisco ISE for a company’s guest user services. Drag and drop the Cisco ISE persona on the left onto its function on the right.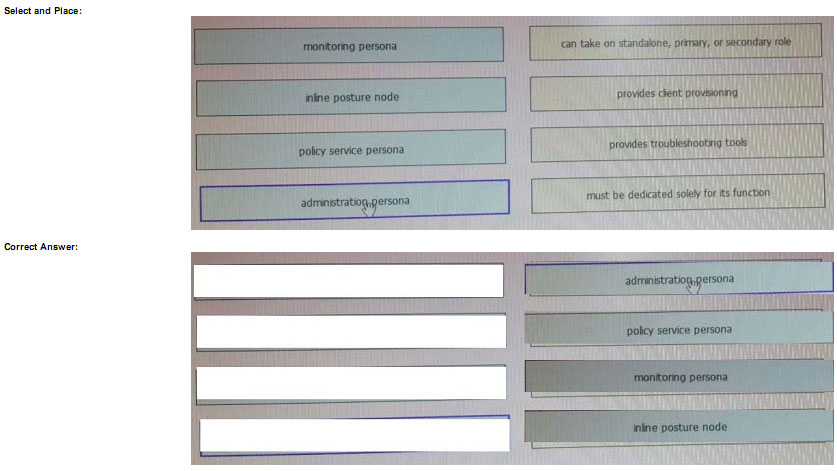 Explanation
Explanation
Explanation/Reference:
QUESTION 49
DRAG DROP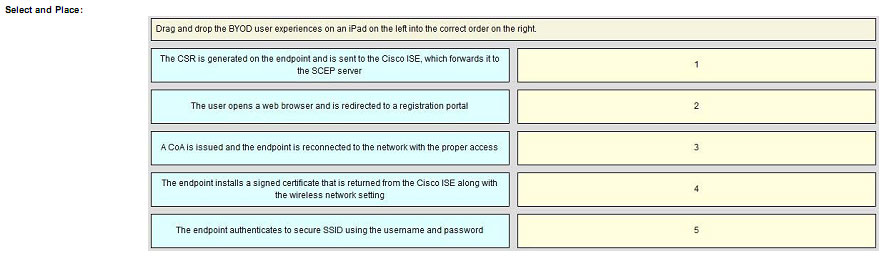
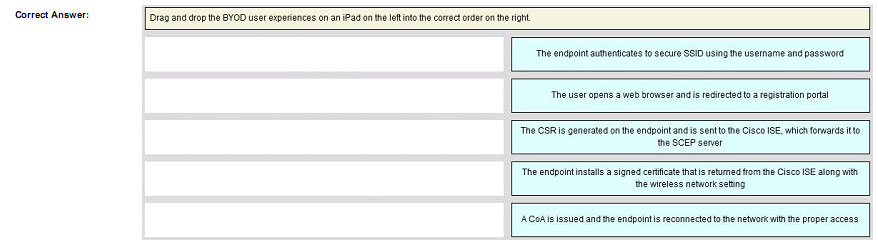 Explanation
Explanation
Explanation/Reference:
Conclusion:
Congratulations on reading here! Passing the Cisco CCNP Security 300-208 exam is not an easy task, you first need to understand the
details of the exam, and then you have to choose a truly valid 300-208 test material(implementing Cisco Secure Access Solutions (Sisas) v1.0):https://www.pass4itsure.com/300-208.html (q&as:356 PDF + VCE),
finally you need to study hard and get ready for the exam.Choosing pass4itsure will make your Cisco 300-208 exam very easy.
[PDF] Free Cisco CCNP Security 300-208 dumps download from Google Drive: https://drive.google.com/open?id=1bnx5KvgWc2pqM6abxmK1Uephb9tHjAHi
[PDF] Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1Qzc3W-UXHXeCJZQZIsYAVUuIacAB5JWN
pass4itsure Promo Code 15% Off
related: https://www.freecertexam.com/the-best-oracle-1z0-144-dumps/