Yes, this is the best solution!
CompTIA sy0-601 dumps come with both PDF and VCE exercises!
Search data from Google, Youtube, Reddit, and Meta… reveals that a large percentage of candidates are looking for Cisco sy0-601 exam practice materials! their first step through various learning styles
Help them learn the CompTIA sy0-601 exam content by themselves, the second step is to get the latest CompTIA sy0-601 dumps practice materials before the exam to help them easily pass the Cisco sy0-601 certification exam.
PS. This is the most guaranteed way of learning! It is also the best solution to pass the exam successfully!
Next, provide candidates with a free copy of the latest CompTIA sy0-601 dumps practice material:
pass4itsure sy0-601 dumps exam materials shared online
| From | Number of exam questions | Type | Associated certification |
| pass4itsure | 15/1146 | Free | CompTIA Security+ 2023 |
Question 1:
A company recenty experienced an attack during which its main website was Girected to the attacker\’s web server, allowing the attacker to harvest credentials trom unsuspecting customers.
Which of the following should the company implement lo prevent this type of attack from occurring In the future?
A. IPSec
B. SSL/TLS
C. ONSSEC
D. SMIME
Correct Answer: B
Question 2:
A company recently decided to allow its employees to use their personally owned devices for tasks like checking email and messaging via mobile applications. The company would like to use MDM, but employees are concerned about the loss of personal data.
Which of the following should the IT department implement to BEST protect the company against company data loss while still addressing the employees\’ concerns?
A. Enable the remote-wiping option in the MDM software in case the phone is stolen.
B. Configure the MDM software to enforce the use of PINs to access the phone.
C. Configure MDM for FDE without enabling the lock screen.
D. Perform a factory reset on the phone before installing the company\’s applications.
Correct Answer: B
Question 3:
After entering a username and password, an administrator must draw a gesture on a touch screen. Which of the following demonstrates what the administrator is providing?
A. Multifactor authentication
B. Something you can do
C. Biometric
D. Two-factor authentication
Correct Answer: B
Question 4:
A user is trying to upload a tax document, which the corporate finance department requested, but a security program IS prohibiting the upload A security analyst determines the file contains Pll, Which of the following steps can the analyst take to correct this issue?
A. Create a URL filter with an exception for the destination website.
B. Add a firewall rule to the outbound proxy to allow file uploads
C. Issue a new device certificate to the user\’s workstation.
D. Modify the exception list on the DLP to allow the upload
Correct Answer: D
Explanation: Data Loss Prevention (DLP) policies are used to identify and protect sensitive data, and often include a list of exceptions that allow certain types of data to be uploaded or shared.
By modifying the exception list on the DLP, the security analyst can allow the tax document to be uploaded without compromising the security of the system. (Reference: CompTIA Security+ SY0-601 Official Textbook, page 479-480)
Question 5:
A software developer needs to perform code-execution testing, black-box testing, and non-functional testing on a new product before its general release. Which of the following BEST describes the tasks the developer is conducting?
A. Verification
B. Validation
C. Normalization
D. Staging
Correct Answer: B
Per geeksforgeeks.org, Methods used in validation are Black Box Testing, White Box Testing, and non-functional testing.
Question 6:
A financial analyst has been accused of violating the company\’s AUP and there is forensic evidence to substantiate the allegation, Which of the following would dispute the analyst\’s claim of innocence?
A. Legal hold
B. Order of volatility
C. Non-repudiation
D. Chain of custody
Correct Answer: C
Chapter 30 Digital Forensics Nonrepudiation Nonrepudiation is a characteristic that refers to the inability to deny an action has taken place. This can be a very important issue in transactions via computers that involve money or things of value.
Question 7:
A company is upgrading its wireless infrastructure to WPA2-Enterprise using EAP-TLS. Which of the following must be part of the security architecture to achieve AAA? (Select TWO)
A. DNSSEC
B. Reverse proxy
C. VPN concentrator
D. PKI
E. Active Directory
F. RADIUS
Correct Answer: DF
Developing a robust WPA2-Enterprise network requires additional tasks, like setting up a PKI or CA (Certificate Authority), to seamlessly distribute certificates to users.
But contrary to what you might think, you can make any of these upgrades without buying new hardware or making changes to the infrastructure.
For example, rolling out guest access or changing the authentication method can be accomplished without additional infrastructure.
Recently, many institutions have been switching EAP methods from PEAP to EAP-TLS after seeing noticeable improvement in connection time and roaming ability or switching from a physical RADIUS server to a Cloud RADIUS solution.
Improving the functionality of wireless networks can be gained without changing a single piece of hardware.
Question 8:
Which of the following control sets should a well-written BCP include? (Select THREE)
A. Preventive
B. Detective
C. Deterrent
D. Corrective
E. Compensating
F. Physical
G. Recovery
Correct Answer: ADG
Question 9:
The manager who is responsible for a data set has asked a security engineer to apply encryption to the data on a hard disk. The security engineer is an example of a:
A. data controller.
B. data owner
C. data custodian.
D. data processor
Correct Answer: C
From the official CompTIA Security+ Study Guide glossary:
data custodian – An individual who is responsible for managing the system on which data assets are stored, including being responsible for enforcing access control, encryption, and backup/recovery measures.
Question 10:
Aconbgany uses a drone for precise perimeter and boundary monitoring. Which of the following should be MOST concerning to the company?
A. Privacy
B. Cloud storage of telemetry data
C. GPS spoofing
D. Weather events
Correct Answer: C
Question 11:
An organization recently released a software assurance policy that requires developers to run code scans each night on the repository.
After the first night, the security team alerted the developers that more than 2,000 findings were reported and needed to be addressed. Which of the following is the MOST likely cause for the high number of findings?
A. The vulnerability scanner was not properly configured and generated a high number of false positives
B. Third-party libraries have been loaded into the repository and should be removed from the codebase.
C. The vulnerability scanner found several memory leaks during runtime, causing duplicate reports for the same issue.
D. The vulnerability scanner was not loaded with the correct benchmarks and needs to be updated.
Correct Answer: A
The most likely cause for the high number of findings is that the vulnerability scanner was not properly configured and generated a high number of false positives.
False positive results occur when a vulnerability scanner incorrectly identifies a non-vulnerable system or application as being vulnerable.
This can happen due to incorrect configuration, over-sensitive rule sets, or outdated scan databases.
Question 12:
Which of the following must be in place before implementing a BCP?
A. SLA
B. AUP
C. NDA
D. BIA
Correct Answer: D
Question 13:
An organization suffered numerous multiday power outages at its current location. The Chief Executive Officer wants to create a disaster recovery strategy to resolve this issue.
Which of the following options offers low-cost solutions? (Choose two.)
A. Warm site
B. Generator
C. Hot site
D. Cold site
E. Cloud backups
F. UPS
Correct Answer: BF
Question 14:
A user attempts to load a web-based application, but the expected login screen does not appear A help desk analyst troubleshoots the issue by running the following command and reviewing the output on the user\’s PC
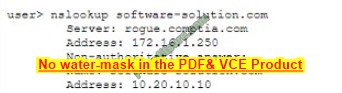
The help desk analyst then runs the same command on the local PC
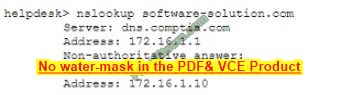
Which of the following BEST describes the attack that is being detected?
A. Domain hijacking
B. DNS poisoning
C. MAC flooding
D. Evil twin
Correct Answer: B
Question 15:
A major clothing company recently lost a large amount of proprietary information.
The security officer must find a solution to ensure this never happens again.
Which of the following is the BEST technical implementation to prevent this from happening again?
A. Configure DLP solutions
B. Disable peer-to-peer sharing
C. Enable role-based access controls.
D. Mandate job rotation.
E. Implement content filters
Correct Answer: A
…
Latest CompTIA SY0-601 exam details
| Exam Name | CompTIA Security+ 2023 |
| Exam Code | SY0-601 |
| Number of Questions | Maximum of 90 questions |
| Type of Questions | Multiple-choice and performance-based |
| Length of Test | 90 minutes |
| Passing Score | 750 (on a scale of 100-900) |
| Languages | English, Japanese, Vietnamese, Thai, Portuguese |
| Testing Provider | Pearson VUE, Testing Centers, Online Testing |
| Price | $392 USD |
| Retirement | July 2024 |
| Replace | SY0-701 (Launch Date: November 7, 2023 ) |
Summarize:
According to CompTIA statistics, since the association was founded, more than 2.2 million people have obtained CompTIA certification. More people will be certified in the future! So will you be one of them?
pass4itsure recommends the best study plan for the CompTIA sy0-601 exam to help you become a member of CompTIA. You only need two steps: The first step is to complete the study of CompTIA sy0-601 exam knowledge, which is helpful for your career planning!
In the second step, use the CompTIA sy0-601 dumps practice material to help you prepare before the exam, because it can guarantee you 100% success in passing the exam.