No one wants to score poor grades or fail the 98-367 exam, it all depends on your decision, nothing more. The success of the 98-367 exam can have a big impact on your career, especially if you are an IT professional. Many IT professionals want success, but they fail. Just because of their choice, but if you get the latest 98-367 study materials, you can easily achieve excellent results in the 98-367 exam. https://www.pass4itsure.com/98-367.html help you easy to pass.Real 98-367 Dumps from pass4itsure.com.

98-367 Exam Overview
Security Fundamentals

Candidates are expected to have some hands-on experience with Windows Server, Windows-based networking, Active Directory, anti-malware products, firewalls, network topologies and devices, and network ports.It can serve as a stepping stone to the Microsoft Certified Solutions Associate (MCSA) exams.
Expertise required for 98-367 Exam:
- Understand security layers (25–30%)
- Understand operating system security (35-40%)
- Understand network security (20–25%)
- Understand security software (15–20%)
Who Benefits
- Candidates with basic safety knowledge and skills
This maybe you’re interested
Key Learning Areas: Understand operating system security

Understand user authentication:Multifactor authentication; physical and virtual smart cards; Remote Authentication Dial-In User Service (RADIUS); biometrics; use Run As to perform administrative tasks
Understand permissions:File system permissions; share permissions; registry; Active Directory; enable or disable inheritance; behavior when moving or copying files within the same disk or on another disk; multiple groups with different permissions; basic permissions and advanced permissions; take ownership; delegation; inheritance
Understand password policies:Password complexity; account lockout; password length; password history; time between password changes; enforce by using Group Policies; common attack methods; password reset procedures; protect domain user account passwords
Understand audit policies:Types of auditing; what can be audited; enable auditing; what to audit for specific purposes; where to save audit information; how to secure audit information
Understand encryption:Encrypting file system (EFS); how EFS-encrypted folders impact moving/copying files; BitLocker (To Go); TPM; software-based encryption; MAIL encryption and signing and other uses; virtual private network (VPN); public key/private key; encryption algorithms; certificate properties; certificate services; PKI/certificate services infrastructure; token devices; lock down devices to run only trusted applications
Understand malware:Buffer overflow; viruses, polymorphic viruses; worms; Trojan horses; spyware; ransomware; adware; rootkits; backdoors; zero day attacks
The importance of completing MTA certification:
Successfully passed the 98-367 exam to get the MTA certification. MTA certification provides the foundation necessary to obtain certification from Microsoft Certified Solution Partners (MCSA) or Microsoft Certified Solution Developer (MCSD). MTA certification creates a new entry point to help people who are not familiar with IT start their careers.
Tips for Success | 98-367 Exam
| 1.Be prepared before the exam so that you can relax on the day of the exam and focus on taking the exam yourself. Conduct long-term testing. |
| 2. I learned a lot from testing. Sometimes, in part of the test, the test will teach you what you need to know in another part of the test. Look for contextual clues that can help you determine the right direction and make no obvious mistakes. |
Why? Microsoft 98-367 dump Pdf

Free microsoft 98-367 pdf dumps download from Google Drive:
https://drive.google.com/open?id=1rDEfb35al1XD5AqRdKT5KY-EkFZWKEWy
Since the 98-367 pdf dump contains advanced concepts, there is a lot of help that will help you get a detailed “Security Fundamentals ” assessment.To receive the Microsoft 98-367 certification exam, you must obtain the latest Microsoft 98-367 exam dump from the website pass4itsure.
Get The Microsoft 98-367 Pdf Questions

Advised to get the Microsoft 98-367 practice exam questions.That’s since this Introduction to Security Fundamentals questions pdf consists from the real exam interface.
QUESTION 1
Which of the following types of viruses protects itself from antivirus programs and is more difficult to trace?
A. Armored virus
B. MBR virus
C. Boot sector virus
D. Macro virus
Correct Answer: A
An armored virus is designed to stop antivirus researchers from examining its code by using various methods to make
tracing and disassembling difficult. This type of virus also protects itself from antivirus programs, making it more difficult
to trace. Answer: D is incorrect. A macro virus is a virus that consists of a macro code which infects the system. A
Macro virus can infect a system rapidly. Since this virus has VB event handlers, it is dynamic in nature and displays
random activation. The victim has only to open a file having a macro virus in order to infect the system with the virus.
DMV, Nuclear, and Word Concept are some good examples of macro viruses. Answer: C is incorrect. A boot sector
virus infects the master boot files of the hard disk or floppy disk. Boot record programs are responsible for booting the
operating system. The boot sector virus copies these programs into another part of the hard disk or overwrites these
files. Answer: B is incorrect. A Master boot record (MBR) virus replaces the boot sector data with its own malicious
code. Every time when the computer starts up, the boot sector virus executes.
QUESTION 2
Which of the following is a use of Microsoft Windows Malicious Software Removal Tool?
A. To gain unauthorized remote access to a computer and launch additional attacks.
B. To distribute itself automatically from one computer to another via network connections.
C. To remove the malware.
D. To perform repetitive or time-consuming task on a network.
Correct Answer: C
Microsoft Windows Malicious Software Removal Tool is used to remove the malware.
Answer: D is incorrect. A bot is defined as a program that is used to perform repetitive or time- consuming task on a
network. Answer: A is incorrect. Rootkit is used to gain unauthorized remote access to a computer and launch
additional
attacks.
Answer: B is incorrect. A worm can automatically distribute itself from one computer to another via network
connections.
QUESTION 3
Mark works as a Network Administrator fot Blue Well Inc. The company has a Windows-based network. Mark is facing a
series of problems with email spam and identifying theft via phishing scams. He wants to implement the various security
measures and to provide some education because it is related to the best practices while using email. Which of the
following can Mark use to minimize the spam amount that is hitting the Microsoft Exchange server of the company?
A. Enable reverse DNS lookup
B. Use Read-only Domain Controller
C. Add Sender Policy Framework
D. Permit User Account Control
Correct Answer: A
To minimize the amount of spam that is hitting the Microsoft Exchange server, it is required to enable reverse DNS
lookup on the SMTP virtual server. It forces a system to crosscheck the domain name with a PTR record (IP address
associated with the domain name) and if the IP address is not matched the record associated with that domain name, it
will not delivered.
Answer: C is incorrect. SPF is used to permit the administrator to configure the server to establish who is acceptable to
send email from their domain. Answer: D is incorrect. User Account Control (UAC) is a technology and security
infrastructure introduced with Microsoft\\’s Windows Vista and Windows Server 2008 operating systems, with a more
relaxed version also present in Windows 7 and Windows Server 2008 R2. It aims to improve the security of Microsoft
Windows by limiting application software to standard user privileges until an administrator authorizes an increase or
elevation.
Answer: B is incorrect. Read-only Domain Controller (RODC) is a domain controller that hosts the read-only partition of
the Active Directory database. RODC was developed by Microsoft typically to be deployed in a branch office
environment.
RODC is a good option to enhance security by placing it in a location where physical security is poor. RODC can also
be placed at locations having relatively few users and a poor network bandwidth to the main site. As only the read-only
partition of the Active Directory database is hosted by RODC, a little local IT knowledge is required to maintain it.
QUESTION 4
You are trying to connect to an FTP server on the Internet from a computer in a school lab. You cannot get a
connection. You try on another computer with the same results. The computers in the lab are able to browse the
Internet.
You are able to connect to this FTP server from home.
What could be blocking the connection to the server?
A. A layer-2 switch
B. A wireless access point
C. A firewall
D. A layer-2 hub
Correct Answer: C
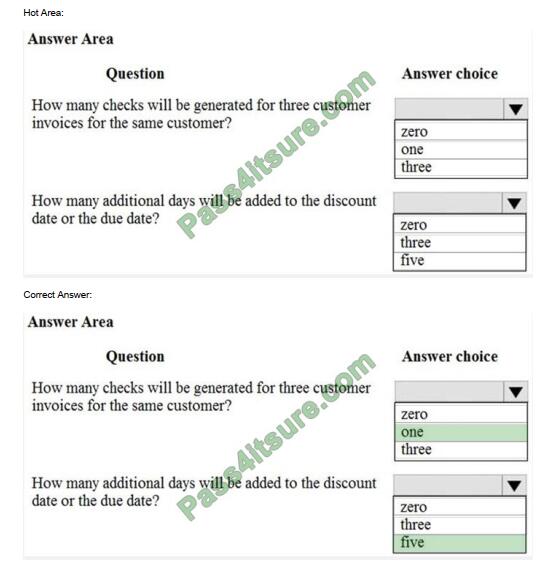
QUESTION 5
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area:

Correct Answer:

QUESTION 6
Which of the following are required to enable for preventing the users from downloading and installing software from the
Internet? Each correct answer represents a complete solution. Choose all that apply.
A. Software restriction policies
B. PTR record
C. User Account Control
D. Anti-Virus software
Correct Answer: AC
Answer: C and A
It is required to enable User Account Control on all Windows 7 computers and to configure software restriction policies
to prevent the users from downloading and installing software from the Internet.
QUESTION 7
Sam works as a Web Developer for McRobert Inc. He wants to control the way in which a Web browser receives
information and downloads content from Web sites. Which of the following browser settings will Sam use to accomplish
this?
A. Security
B. Certificate
C. Cookies
D. Proxy server
Correct Answer: A
The Web browser\\’s Security setting controls the way in which a Web browser receives information and downloads
content from Web sites. In Internet Explorer, users can access the Security setting from Tools menu > Internet Options
>
Security tab page.
Answer: C is incorrect. A cookie is a small bit of text that accompanies requests and pages as they move between Web
servers and browsers. It contains information that is read by a Web application, whenever a user visits a site. Cookies
are
stored in the memory or hard disk of client computers. A Web site stores information, such as user preferences and
settings in a cookie. This information helps in providing customized services to users. There is absolutely no way a
Web
server can access any private information about a user or his computer through cookies, unless a user provides the
information. The Web server cannot access cookies created by other Web servers. Answer: D is incorrect. Proxy server
setting is used to connect to the Internet through a proxy server.
QUESTION 8
Which of the following applications captures network packets as they traverse a network and displays them to the
attacker?
A. Keylogger
B. Sniffer
C. Key fob
D. Protocol analyzer
Correct Answer: B
A sniffer is a software tool that is used to capture any network traffic. Since a sniffer changes the NIC of the LAN card
into promiscuous mode, the NIC begins to record incoming and outgoing data traffic across the network. A sniffer attack
is
a passive attack because the attacker does not directly connect with the target host. This attack is most often used to
grab logins and passwords from network traffic. Tools such as Ethereal, Snort, Windump, EtherPeek, Dsniff are some
good
examples of sniffers. These tools provide many facilities to users such as graphical user interface, traffic statistics
graph, multiple sessions tracking, etc. Answer: D is incorrect. A protocol analyzer for particular types of networks is a
computer
software or computer hardware that can intercept and log traffic passing over a digital network or part of a network. As
data streams flow across the network, the protocol analyzer captures each packet and, if needed, decodes and
analyzes
its content according to the appropriate RFC or other specifications.
Answer: A is incorrect. A keylogger is a software tool that traces all or specific activities of a user on a computer. Once a
keylogger is installed on a victim\\’s computer, it can be used for recording all keystrokes on the victim\\’s computer in a
predefined log file. An attacker can configure a log file in such a manner that it can be sent automatically to a predefined
e-mail address. Some of the main features of a keylogger are as follows:
It can record all keystrokes.
It can capture all screenshots.
It can record all instant messenger conversations. It can be remotely installed.
It can be delivered via FTP or e-mail.
Answer: C is incorrect. Key fobs are security devices used by telecommuters to provide one part of a three way match
for a user to log on to a secured network.

These are display-only devices that algorithmically generate security codes as part of a challenge/response authentication system. This code usually changes very quickly and is used with the PIN for authentication.
QUESTION 9
Mark works as a Network Administrator for TechMart Inc. The company has a Windows-based network. Mark wants to
implement stronger authentication measures for the customers, as well as eliminate IT staff from logging on with high
privileges. Mark has various options, but he is required to keep the processes easy for the helpdesk staff. Which of the
following is a service can the staff uses as an alternative of signing in with elevate privileges?
A. Secondary Logon-Run As
B. Security log
C. Hardware firewall
D. Encrypted network configuration
Correct Answer: A
Secondary Logon (Run As) is defined as a starting programs and tools in local administrative context. Windows
secondary logon is used to permit administrators to log on with a non-administrative account and be able to perform the
several administrative tasks without logging off by using trusted administrative programs in administrative contexts.
Answer: B is incorrect. The security log is generated by a firewall or other security device. It is used to define list of
events that could affect the security of data or infrastructure, such as access attempts or commands, and the names of
the users participating in this illegal process. Answer: C is incorrect. Hardware firewall is defined as the important part of
the system and network set-up on a broadband connection. It can be effective with small or no configuration, and is
used to protect every machine on a local network. The hardware firewalls will have at least four network ports for
connecting to other computers. This type of firewall uses packet filtering for checking the header of a packet in order to
check its source and destination. The information obtained in this manner is compared to a set of predefined or usercreated rules and then the packet is forwarded or dropped.
QUESTION 10
You are trying to enable BitLocker on your father\\’s computer.
What is the purpose of the Trusted Platform Module (TPM) when it is used by BitLocker?
A. to store an encrypted file allocation table for the protected drive
B. to provide a co-processor that encrypts/decrypts data
C. to verify the integrity of the early boot components
D. to store the hashed data produced by BitLocker encryption
Correct Answer: C
QUESTION 11
Mark works as a Desktop Administrator for TechMart Inc. The company has a Windows-based network. He has bees
assigned a project to upgrade the browsers to Internet Explorer (IE) 8 for working with the latest Internet technologies
Mark wants to ensure that the company uses a number of the security features built into the browser while maintaining
functionality within the company\\’s intranet. Mark is also educating his users to be good Internet citizens and use the
safe web sur?ng. Mark asked his team to be assured that they are on a secured website. What they will do?
A. Take a look for a padlock in the lower right corner of the browser and https:// in the address bar.
B. Provide protection against a Distributed Denial of Services attack.
C. Call a team member while behaving to be someone else for gaining access to sensitive information.
D. Go into the Internet Options, select the Security, and add the intranet site to the list of Local Intranet Site.
Correct Answer: A
To be sure that the team members are on a secure site, they are required to look for a padlock in the lower right corner
of the browser and https:// in the address bar. It will not guarantee that the site is secure but can be used. Answer: D is
incorrect. The Internet zone feature in IE 8 can be configured and users are enabled to easily browse the local intranet
without disturbing the security levels by using the following steps: 1.Go into the Internet Options and select the Security.
2.Add the intranet site to the list of Local Intranet Site. Answer: C is incorrect. Social engineering can be defined as any
type of behavior used to inadvertently or deliberately aid an attacker in gaining access to an authorized user\\’s
password or other sensitive information. Social engineering is the art of convincing people and making them disclose
useful information such as account names and passwords. This information is further exploited by hackers to gain
access to a user\\’s computer or network. This method involves mental ability of people to trick someone rather than
their technical skills. A user should always distrust people who ask him for his account name, password, computer
name, IP address, employee ID, or other information that can be misused. Answer: B While stressing the
Con?dentiality, Integrity, and Availability triangle in the training of users, the process of providing availability is related to
security training to ensure the protection against a Distributed Denial of Services attack.
QUESTION 12
Which two characteristics should you recommend for a user\\’s domain password? (Choose two.)
A. Hard to guess
B. Includes Unicode characters
C. Easy to remember
D. Easy to increment
Correct Answer: AC
Reference: http://www.usewisdom.com/computer/passwords.html
QUESTION 13
Which of the following is a central, secure database in which Windows stores all hardware configuration information,
software configuration information, and system security policies?
A. Registry
B. Program files folder
C. DLL file
D. Configuration file
Correct Answer: A
The registry is a central, secure database in which Windows stores all hardware configuration information, software
configuration information, and system security policies.
The registry is the central storage for all configuration data. It stores Windows operating system configuration, computer
hardware configuration, configuration information about Win32-based applications, and user preferences in a
hierarchical
database file.
Answer: B, C, and D are incorrect. The Program files folder, DLL file, or Configuration file is not a central, secure
database in which Windows stores all hardware configuration information, software configuration information, and
system
security policies.
Please visit variety of question types on Microsoft exams.
Summarize:
With a complete collection of 98-367 exam questions and answers, pass4itsure will take you through the 98-367 dump questions and answers to prepare for your exam. In the 98-367 exam, https://www.pass4itsure.com/98-367.html gathered the real exam questions and their answers so that you can prepare and pass the exam.