Cisco CCNP Security 300-209 dumps pdf,300-209 Practice Test Questions
Cabinetdetherapies collects 50 authentic Cisco CCNP Security 300-209 Exam questions and Answers, and 300-209 pdf online sharing downloads, we help you improve your skills if you want to pass Cisco 300-209 Exams need to be noted: (Duration 90 minutes (65 – 75 questions)),(available Languages English, Japanese), Exam Policies. It is recommended, but not required, that students have the following knowledge and skills:
- Knowledge of Microsoft Windows® operating system
- A CCNA Security certification
if you want to get “Implementing Cisco Secure Mobility Solutions (SIMOS) v1.0” is the 300-209 exam dump, CISCO 300-209 exam certification.
Cabinetdetherapies recommends that you: https://www.geekcert.com/300-209.html (Q&As: 393 PDF + VCE) is frequently updated and reviewed to pass the exam quickly.
[PDF]Free Cisco CCNP Security 300-209 dumps download from Google Drive: https://drive.google.com/open?id=1MYSeWmuvxbdVhJPeADLQgrXqZHCC4ua2
[PDF]Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1Qzc3W-UXHXeCJZQZIsYAVUuIacAB5JWN
300-209 SIMOS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/specialist-simos.html
Free 50 Cisco CCNP Security 300-209 Practice test questions and answers
QUESTION 1
Which command will prevent a group policy from inheriting a filter ACL in a clientless SSL VPN?
A. vpn-filter none
B. no vpn-filter
C. filter value none
D. filter value ACLname
Correct Answer: C
Explanation
Explanation/Reference:
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa-command-reference/T- Z/cmdref4/v.html#pgfId-1842564
QUESTION 2
A Cisco IOS SSL VPN gateway is configured to operate in clientless mode so that users can access file shares on a Microsoft Windows 2003 server. Which protocol is used between the Cisco IOS router and the Windows server?
A. HTTPS
B. NetBIOS
C. CIFS
D. HTTP
Correct Answer: C
Explanation
QUESTION 3
A rogue static route is installed in the routing table of a Cisco FlexVPN and is causing traffic to be blackholed. Which command should be used to identify the peer from which that route originated?
A. show crypto ikev2 sa detail
B. show crypto route
C. show crypto ikev2 client flexvpn
D. show ip route eigrp
E. show crypto isakmp sa detail
Correct Answer: B
Explanation
QUESTION 4
Authorization of a clientless SSL VPN defines the actions that a user may perform within a clientless SSL VPN session. Which statement is correct concerning the SSL VPN authorization process?
A. Remote clients can be authorized by applying a dynamic access policy, which is configured on an external AAA server.
B. Remote clients can be authorized externally by applying group parameters from an external database.
C. Remote client authorization is supported by RADIUS and TACACS+ protocols.
D. To configure external authorization, you must configure the Cisco ASA for cut-through proxy.
Correct Answer: B
Explanation
Explanation/Reference:
CISCO SSL VPN guide
The aaa authentication command is entered to specify an authentication list or server group under a SSL VPN context configuration. If this command is not configured and AAA is configured globally on the router, global authentication will be
applied to the context configuration.
The database that is configured for remote-user authentication on the SSL VPN gateway can be a local database, or the database can be accessed through any RADIUS or TACACS+ AAA server.
We recommend that you use a separate AAA server, such as a Cisco Access Control Server (ACS). A separate AAA server provides a more robust security solution. It allows you to configure unique passwords for each remote user and
accounting and logging for remote-user sessions.
QUESTION 5
Refer to the exhibit.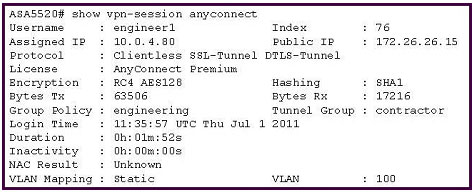
A NOC engineer needs to tune some postlogin parameters on an SSL VPN tunnel.
From the information shown, where should the engineer navigate to, in order to find all the postlogin session parameters?
A. “engineering” Group Policy
B. “contractor” Connection Profile
C. DefaultWEBVPNGroup Group Policy
D. DefaultRAGroup Group Policy
E. “engineer1” AAA/Local Users
Correct Answer: A
Explanation
Explanation/Reference:
Explanation: http://www.cisco.com/en/US/docs/ios/12_4t/12_4t11/ htwebvpn.html#wp1054618
The policy group is a container that defines the presentation of the portal and the permissions for resources that are configured for a group of remote users. Entering the policy group command places the router in webvpn group policy
configuration mode. After it is configured, the group policy is attached to the SSL VPN context configuration by configuring the default-group-policy command.
The following tasks are accomplished in this configuration:
The presentation of the SSL VPN portal page is configured.
A NetBIOS server list is referenced.
A port-forwarding list is referenced.
The idle and session timers are configured.
A URL list is referenced.
QUESTION 6
Which equation describes an elliptic curve?
A. y3 = x3 + ax + b
B. x3 = y2 + ab + x
C. y4 = x2 + ax + b
D. y2 = x3 + ax + b
E. y2 = x2 + ax + b2
Correct Answer: D
Explanation
QUESTION 7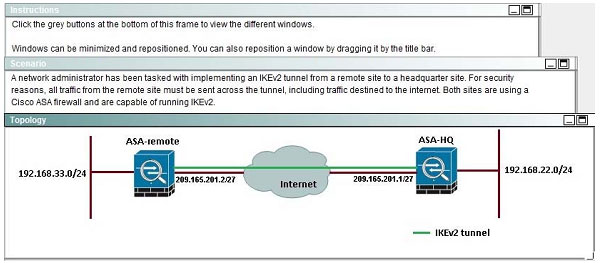
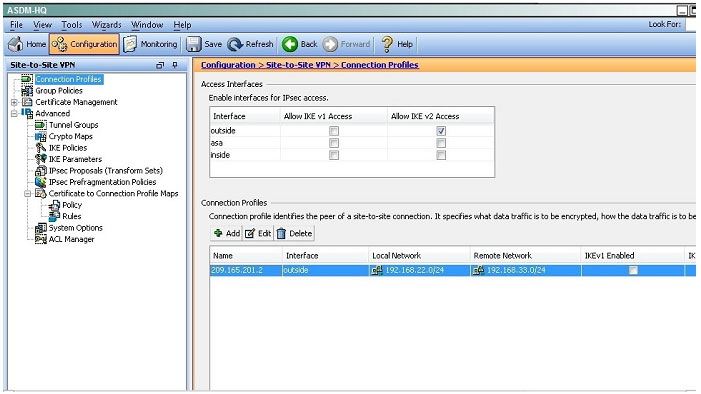
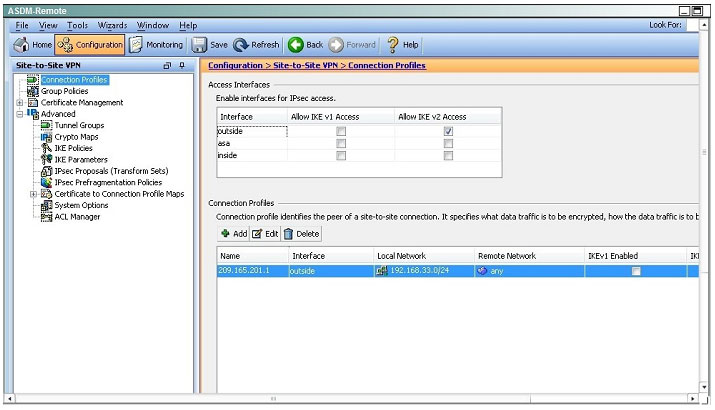 When a tunnel is initiated by the headquarter ASA, which one of the following Diffie- Hellman groups is selected by the headquarter ASA during CREATE_CHILD_SA exchange?
When a tunnel is initiated by the headquarter ASA, which one of the following Diffie- Hellman groups is selected by the headquarter ASA during CREATE_CHILD_SA exchange?
A. 1
B. 2
C. 5
D. 14
E. 19
Correct Answer: C
Explanation
Explanation/Reference:
Traffic initiated by the HQ ASA is assigned to the static outside crypto map, which shown below to use DH group 5 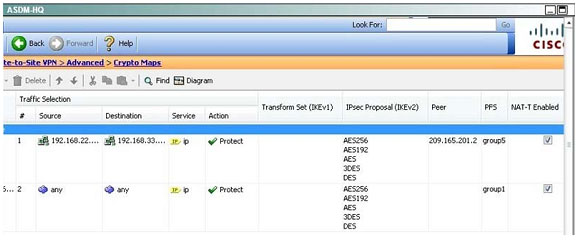
QUESTION 8
Which three changes must be made to migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured? (Choose three.)
A. Enable EIGRP next-hop-self on the hub.
B. Disable EIGRP next-hop-self on the hub.
C. Enable EIGRP split-horizon on the hub.
D. Add NHRP redirects on the hub.
E. Add NHRP shortcuts on the spoke.
F. Add NHRP shortcuts on the hub.
Correct Answer: ADE
Explanation
QUESTION 9
Which cryptographic algorithms are a part of the Cisco NGE suite?
A. HIPPA DES
B. AES-CBC-128
C. RC4-128
D. AES-GCM-256
Correct Answer: D
Explanation
Explanation/Reference:
Reference:
https://www.cisco.com/web/learning/le21/le39/docs/tdw166_prezo.pdf
QUESTION 10
Which Cisco ASDM option configures forwarding syslog messages to email?
A. Configuration > Device Management > Logging > E-Mail Setup
B. Configuration > Device Management > E-Mail Setup > Logging Enable
C. Select the syslogs to email, click Edit, and select the Forward Messages option.
D. Select the syslogs to email, click Settings, and specify the Destination Email Address option.
Correct Answer: A
Explanation
QUESTION 11
Your corporate finance department purchased a new non-web-based TCP application tool to run on one of its servers. Certain finance employees need remote access to the software during nonbusiness hours. These employees do not have
“admin” privileges to their PCs.
What is the correct way to configure the SSL VPN tunnel to allow this application to run?
A. Configure a smart tunnel for the application.
B. Configure a “finance tool” VNC bookmark on the employee clientless SSL VPN portal.
C. Configure the plug-in that best fits the application.
D. Configure the Cisco ASA appliance to download the Cisco AnyConnect SSL VPN Client to the finance employee each time an SSL VPN tunnel is established.
Correct Answer: A
Explanation
Explanation/Reference:
http://www.cisco.com/en/US/docs/security/asa/asa80/configuration/guide/webvpn.html
A smart tunnel is a connection between a TCP-based application and a private site, using a clientless (browser based) SSL VPN session with the security appliance as the pathway, and the security appliance as a proxy server. You can
identify applications to which you want to grant smart tunnel access, and specify the local path to each application. For applications running on Microsoft Windows, you can also require a match of the SHA-1 hash of the checksum as a
condition for granting smart tunnel access.
Lotus SameTime and Microsoft Outlook Express are examples of applications to which you might want to grant smart tunnel access.
Configuring smart tunnels requires one of the following procedures, depending on whether the application is a client or is a web-enabled application:
•Create one or more smart tunnel lists of the client applications, then assign the list to the group policies or local user policies for whom you want to provide smart tunnel access.
•Create one or more bookmark list entries that specify the URLs of the web-enabled applications eligible for smart tunnel access, then assign the list to the DAPs, group policies, or local user policies for whom you want to provide smart tunnel
access.
You can also list web-enabled applications for which to automate the submission of login credentials in smart tunnel connections over clientless SSL VPN sessions.
Why Smart Tunnels?
Smart tunnel access lets a client TCP-based application use a browser-based VPN connection to connect to a service. It offers the following advantages to users, compared to plug-ins and the legacy technology, port forwarding:
•Smart tunnel offers better performance than plug-ins.
•Unlike port forwarding, smart tunnel simplifies the user experience by not requiring the user connection of the local application to the local port.
•Unlike port forwarding, smart tunnel does not require users to have administrator privileges.
The advantage of a plug-in is that it does not require the client application to be installed on the remote computer.
Smart Tunnel Requirements, Restrictions, and Limitations
The following sections categorize the smart tunnel requirements and limitations.
General Requirements and Limitations
Smart tunnel has the following general requirements and limitations:
•The remote host originating the smart tunnel must be running a 32-bit version of Microsoft Windows Vista, Windows XP, or Windows 2000; or Mac OS 10.4 or 10.5.
•Smart tunnel auto sign-on supports only Microsoft Internet Explorer on Windows.
•The browser must be enabled with Java, Microsoft ActiveX, or both.
•Smart tunnel supports only proxies placed between computers running Microsoft Windows and the security appliance. Smart tunnel uses the Internet Explorer configuration (that is, the one intended for system-wide use in Windows). If the
remote computer requires a proxy server to reach the security appliance, the URL of the terminating end of the connection must be in the list of URLs excluded from proxy services. If the proxy configuration specifies that traffic destined for the
ASA goes through a proxy, all smart tunnel traffic goes through the proxy.
In an HTTP-based remote access scenario, sometimes a subnet does not provide user access to the VPN gateway. In this case, a proxy placed in front of the ASA to route traffic between the web and the end user’s location provides web
access. However, only VPN users can configure proxies placed in front of the ASA.
When doing so, they must make sure these proxies support the CONNECT method. For proxies that require authentication, smart tunnel supports only the basic digest authentication type.
•When smart tunnel starts, the security appliance by default passes all browser traffic through the VPN session if the browser process is the same. The security appliance also does this if a tunnel-all policy applies. If the user starts another
instance of the browser process, it passes all traffic through the VPN session. If the browser process is the same and the security appliance does not provide access to a URL, the user cannot open it. As a workaround, assign a tunnel policy
that is not tunnel-all.
•A stateful failover does not retain smart tunnel connections. Users must reconnect following a failover.
QUESTION 12
Which two options are purposes of the key server in Cisco IOS GETVPN? (Choose two.)
A. to define group members.
B. to distribute static routing information.
C. to distribute dynamic routing information.
D. to encrypt transit traffic.
Correct Answer: AD
Explanation
QUESTION 13
Which command identifies an AnyConnect profile that was uploaded to the router flash?
A. crypto vpn anyconnect profile SSL_profile flash:simos-profile.xml
B. svc import profile SSL_profile flash:simos-profile.xml
C. anyconnect profile SSL_profile flash:simos-profile.xml
D. webvpn import profile SSL_profile flash:simos-profile.xml
Correct Answer: A
Explanation
QUESTION 14
A custom desktop application needs to access an internal server. An administrator is tasked with configuring the company’s SSL VPN gateway to allow remote users to work. Which two technologies would accommodate the company’s
requirement? (Choose two).
A. AnyConnect client
B. Smart Tunnels
C. Email Proxy
D. Content Rewriter
E. Portal Customizations
Correct Answer: AB
Explanation
QUESTION 15
Refer to the exhibit.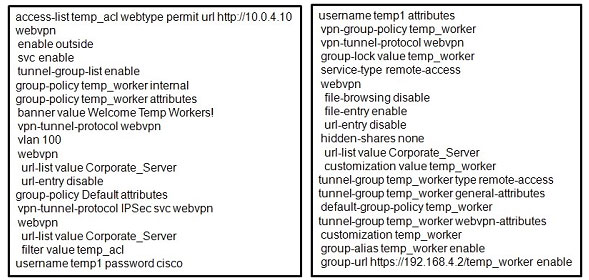 A junior network engineer configured the corporate Cisco ASA appliance to accommodate a new temporary worker. For security reasons, the IT department wants to restrict the internal network access of the new temporary worker to the
A junior network engineer configured the corporate Cisco ASA appliance to accommodate a new temporary worker. For security reasons, the IT department wants to restrict the internal network access of the new temporary worker to the
corporate server, with an IP address of 10.0.4.10. After the junior network engineer finished the configuration, an IT security specialist tested the account of the temporary worker. The tester was able to access the URLs of additional secure
servers from the WebVPN user account of the temporary worker.
What did the junior network engineer configure incorrectly?
A. The ACL was configured incorrectly.
B. The ACL was applied incorrectly or was not applied.
C. Network browsing was not restricted on the temporary worker group policy.
D. Network browsing was not restricted on the temporary worker user policy.
Correct Answer: B
Explanation
QUESTION 16
Which three remote access VPN methods in an ASA appliance provide support for Cisco Secure Desktop? (Choose three.)
A. IKEv1
B. IKEv2
C. SSL client
D. SSL clientless
E. ESP
F. L2TP
Correct Answer: BCD
Explanation
QUESTION 17
You have been using pre-shared keys for IKE authentication on your VPN. Your network has grown rapidly, and now you need to create VPNs with numerous IPsec peers. How can you enable scaling to numerous IPsec peers?
A. Migrate to external CA-based digital certificate authentication.
B. Migrate to a load-balancing server.
C. Migrate to a shared license server.
D. Migrate from IPsec to SSL VPN client extended authentication.
Correct Answer: A
Explanation
QUESTION 18
Which option is a required element of Secure Device Provisioning communications?
A. the introducer
B. the certificate authority
C. the requestor
D. the registration authority
Correct Answer: A
Explanation
QUESTION 19
When troubleshooting clientless SSL VPN connections, which option can be verified on the client PC?
A. address assignment
B. DHCP configuration
C. tunnel group attributes
D. host file misconfiguration
Correct Answer: C
Explanation
QUESTION 20
Which VPN feature allows remote access clients to print documents to local network printers?
A. Reverse Route Injection
B. split tunneling
C. loopback addressing
D. dynamic virtual tunnels
Correct Answer: B
Explanation
QUESTION 21
An engineer has integrated a new DMVPN to link remote offices across the internet using Cisco IOS routers. When connecting to remote sites, pings and voice data appear to flow properly and all tunnel stats seem to show that are up.
However, when trying to connect to a remote server using RDP, the connection fails. Which action resolves this issue?
A. Change DMVPN timeout values.
B. Adjust the MTU size within the routers.
C. Replace certificate on the RDP server.
D. Add RDP port to the extended ACL.
Correct Answer: C
Explanation
QUESTION 22
What command in cli you have to use to capture IKEv1 phase 1
A. capture match ip q port 500 eq port 500
B. capture match gre q port 500 eq port 500
C. apture match ah q port 500 eq port 500
D. capture match udp eq port 153 eq port 153
E. capture match udp eq port 500 eq port 500Correct Answer: E
Explanation
QUESTION 23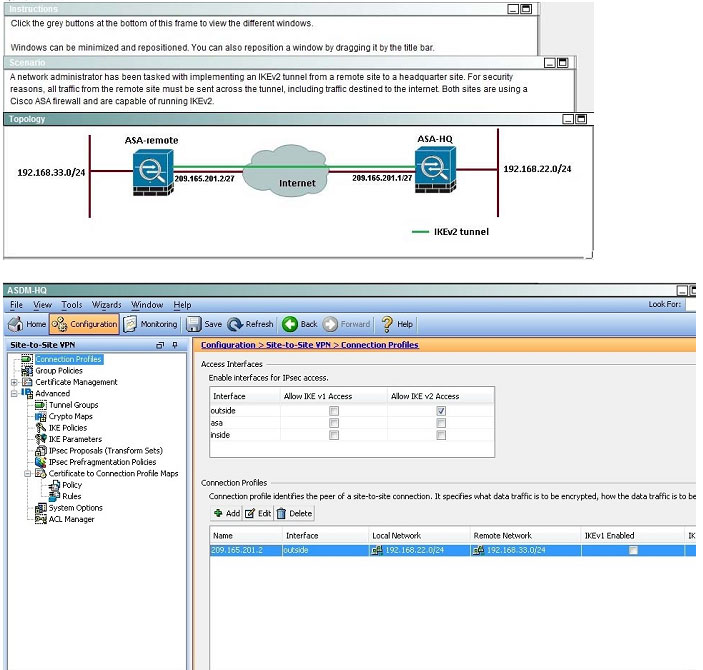
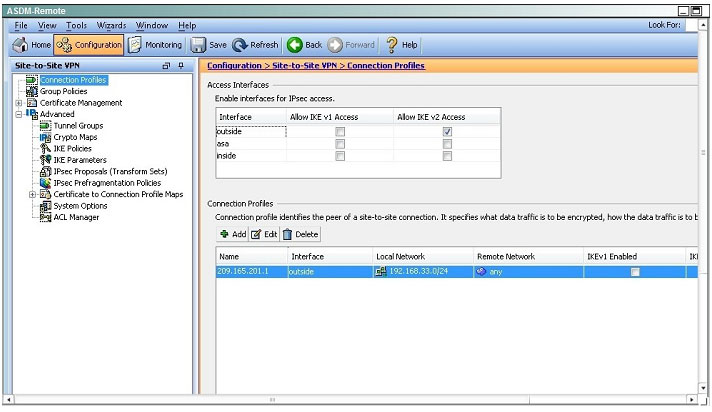 Based on the provided ASDM configuration for the remote ASA, which one of the following is correct?
Based on the provided ASDM configuration for the remote ASA, which one of the following is correct?
A. An access-list must be configured on the outside interface to permit inbound VPN traffic
B. A route to 192.168.22.0/24 will not be automatically installed in the routing table
C. The ASA will use a window of 128 packets (64×2) to perform the anti-replay check _
D. The tunnel can also be established on TCP port 10000
Correct Answer: C
Explanation
Explanation/Reference:
Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence number to each encrypted packet. The decryptor keeps track of which packets it has
seen on the basis of these numbers. Currently, the default window size is 64 packets. Generally, this number (window size) is sufficient, but there are times when you may want to expand this window size. The IPsec Anti-Replay Window:
Expanding and Disabling feature allows you to expand the window size, allowing the decryptor to keep track of more than 64 packets.
QUESTION 24
Which adaptive security appliance command can be used to see a generic framework of the requirements for configuring a VPN tunnel between an adaptive security appliance and a Cisco IOS router at a remote office?
A. vpnsetup site-to-site steps
B. show running-config crypto
C. show vpn-sessiondb l2l
D. vpnsetup ssl-remote-access steps
Correct Answer: A
Explanation
QUESTION 25
Which three types of SSO functionality are available on the Cisco ASA without any external SSO servers? (Choose three.)A. SAML
B. HTTP POST
C. HTTP Basic
D. NTLM
E. Kerberos
F. OAuth 2.0
Correct Answer: BCD
Explanation
QUESTION 26
An engineer has configured Cisco AnyConnect VPN using IKEv2 on a Cisco ISO router. The user cannot connect in the Cisco AnyConnect client, but receives an alert message “Use a browser to gain access.” Which action does the engineer
take to eliminate this issue?
A. Reset user login credentials.
B. Disable the HTTP server.
C. Correct the URL address.
D. Connect using HTTPS.
Correct Answer: C
Explanation
QUESTION 27
Which is used by GETVPN, FlexVPN and DMVPN?
A. NHRP
B. MPLS
C. GRE
D. ESP
Correct Answer: D
Explanation
QUESTION 28
The Cisco AnyConnect client fails to connect via IKEv2 but works with SSL. The following error message is displayed:
“Login Denied, unauthorized connection mechanism, contact your administrator”
What is the most possible cause of this problem?
A. DAP is terminating the connection because IKEv2 is the protocol that is being used.
B. The client endpoint does not have the correct user profile to initiate an IKEv2 connection.
C. The AAA server that is being used does not authorize IKEv2 as the connection mechanism.
D. The administrator is restricting access to this specific user.
E. The IKEv2 protocol is not enabled in the group policy of the VPN headend.
Correct Answer: E
Explanation
QUESTION 29
What are two variables for configuring clientless SSL VPN single sign-on? (Choose two.)
A. CSCO_WEBVPN_OTP_PASSWORD
B. CSCO_WEBVPN_INTERNAL_PASSWORD
C. CSCO_WEBVPN_USERNAME
D. CSCO_WEBVPN_RADIUS_USER
Correct Answer: BC
Explanation
QUESTION 30
Which command is used to determine how many GMs have registered in a GETVPN environment?
A. show crypto isakmp sa
B. show crypto gdoi ks members
C. show crypto gdoi gm
D. show crypto ipsec sa
E. show crypto isakmp sa count
Correct Answer: B
Explanation
QUESTION 31
Which three configuration parameters are mandatory for an IKEv2 profile? (Choose three.)
A. IKEv2 proposal
B. local authentication method
C. match identity or certificate
D. IKEv2 policy
E. PKI certificate authority
F. remote authentication method
G. IKEv2 profile description
H. virtual template
Correct Answer: BCF
Explanation
QUESTION 32
Refer to the exhibit.
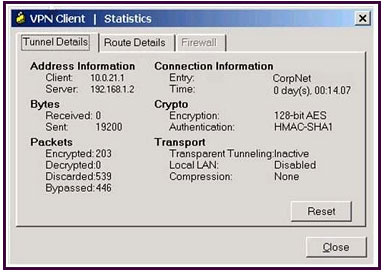
A new NOC engineer is troubleshooting a VPN connection.
Which statement about the fields within the Cisco VPN Client Statistics screen is correct?A. The ISP-assigned IP address of 10.0.21.1 is assigned to the VPN adapter of the PC.
B. The IP address of the security appliance to which the Cisco VPN Client is connected is 192.168.1.2.
C. CorpNet is the name of the Cisco ASA group policy whose tunnel parameters the connection is using.
D. The ability of the client to send packets transparently and unencrypted through the tunnel for test purposes is turned off.
E. With split tunneling enabled, the Cisco VPN Client registers no decrypted packets.
Correct Answer: B
Explanation
QUESTION 33
Which option describes the purpose of the shared argument in the DMVPN interface command tunnel protection IPsec profile ProfileName shared?
A. shares a single profile between multiple tunnel interfaces
B. allows multiple authentication types to be used on the tunnel interface
C. shares a single profile between a tunnel interface and a crypto map
D. shares a single profile between IKEv1 and IKEv2
Correct Answer: A
Explanation
QUESTION 34
Refer to the exhibit.
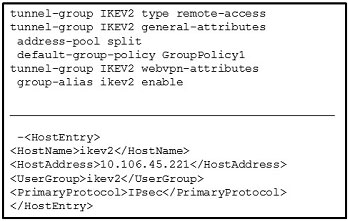
The customer can establish an AnyConnect connection on the first attempt only. Subsequent attempts fail. What might be the issue?
A. IKEv2 is blocked over the path.
B. UserGroup must be different than the name of the connection profile.
C. The primary protocol should be SSL.
D. UserGroup must be the same as the name of the connection profile.
Correct Answer: D
Explanation
QUESTION 35
Which command enables the router to form EIGRP neighbor adjacencies with peers using a different subnet than the ingress interface?
A. ip unnumbered interface
B. eigrp router-id
C. passive-interface interface name
D. ip split-horizon eigrp as number
Correct Answer: A
Explanation
QUESTION 36
Which Cisco adaptive security appliance command can be used to view the count of all active VPN sessions?
A. show vpn-sessiondb summary
B. show crypto ikev1 sa
C. show vpn-sessiondb ratio encryption
D. show iskamp sa detail
E. show crypto protocol statistics all
Correct Answer: A
Explanation
QUESTION 37
Which NGE IKE Diffie-Hellman group identifier has the strongest cryptographic properties?
A. group 10
B. group 24
C. group 5
D. group 20
Correct Answer: D
Explanation
QUESTION 38
An engineer is configuring an IPsec VPN with IKEv2. Which three components are part of the IKEv2 proposal for this implementation? (Choos three.)
A. key ring
B. DH group
C. integrity
D. tunnel name
E. encryption
Correct Answer: CDE
Explanation
QUESTION 39
Remote users want to access internal servers behind an ASA using Microsoft terminal services. Which option outlines the steps required to allow users access via the ASA clientless VPN portal?
A. 1. Configure a static pat rule for TCP port 3389
2. Configure an inbound access-list to allow traffic from remote users to the servers
3. Assign this access-list rule to the group policy
B. 1. Configure a bookmark of the type http:// server-IP :3389
2. Enable Smart tunnel on this bookmark
3. Assign the bookmark to the desired group policy
C. 1. Configure a Smart Tunnel application list
2. Add the rdp.exe process to this list
3. Assign the Smart Tunnel application list to the desired group policy
D. 1. Upload an RDP plugin to the ASA
2. Configure a bookmark of the type rdp:// server-IP
3. Assign the bookmark list to the desired group policy
Correct Answer: D
Explanation
QUESTION 40
Which two RADIUS attributes are needed for a VRF-aware FlexVPN hub? (Choose two.)
A. ip:interface-config=ip unnumbered loobackn
B. ip:interface-config=ip vrf forwarding ivrf
C. ip:interface-config=ip src route
D. ip:interface-config=ip next hop
E. ip:interface-config=ip neighbor 0.0.0.0
Correct Answer: AB
Explanation
QUESTION 41
Which four activities does the Key Server perform in a GETVPN deployment? (Choose four.)
A. authenticates group members
B. manages security policy
C. creates group keys
D. distributes policy/keys
E. encrypts endpoint traffic
F. receives policy/keys
G. defines group members
Correct Answer: ABCD
Explanation
QUESTION 42
Which algorithm provides both encryption and authentication for data plane communication?
A. SHA-96
B. SHA-384
C. 3DES
D. AES-256
E. AES-GCM
F. RC4
Correct Answer: E
Explanation
QUESTION 43
![]()
Refer to the exhibit. An engineer encounters a debug message. Which action can the engineer take to eliminate this error message?
A. Use stronger encryption suite.
B. Correct the VPN peer address.
C. Make adjustment to IPSec replay window.
D. Change the preshared key to match.
Correct Answer: B
Explanation
QUESTION 44
Which command configures IKEv2 symmetric identity authentication?
A. match identity remote address 0.0.0.0
B. authentication local pre-share
C. authentication pre-share
D. authentication remote rsa-sig
Correct Answer: D
Explanation
QUESTION 45
Which configuration is used to build a tunnel between a Cisco ASA and ISR?
A. crypto map
B. DMVPN
C. GET VPN
D. GRE with IPsec
E. GRE without IPsec
Correct Answer: A
Explanation
QUESTION 46
Refer to the exhibit.
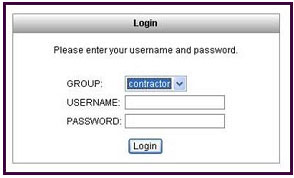
For the ABC Corporation, members of the NOC need the ability to select tunnel groups from a drop-down menu on the Cisco WebVPN login page.
As the Cisco ASA administrator, how would you accomplish this task?
A. Define a special identity certificate with multiple groups, which are defined in the certificate OU field, that will grant the certificate holder access to the named groups on the login page.
B. Under Group Policies, define a default group that encompasses the required individual groups that will appear on the login page.
C. Under Connection Profiles, define a NOC profile that encompasses the required individual profiles that will appear on the login page.
D. Under Connection Profiles, enable “Allow user to select connection profile.”
Correct Answer: D
Explanation
Explanation/Reference:
Cisco ASDM User Guide Version 6.1
Add or Edit SSL VPN Connections > Advanced > SSL VPN This dialog box lets you configure attributes that affect what the remote user sees upon login. Fields ?Login Page Customization–Configures the look and feel of the user login page
by specifying which preconfigured customization attributes to apply. The default is DfltCustomization. ?Manage–Opens the Configure GUI Customization Objects window. ?Connection Aliases–Lists in a table the existing connection aliases
and their status and lets you add or delete items in that table. A connection alias appears on the user login page if the connection is configured to allow users to select a particular connection (tunnel group) at login. ?Add–Opens the Add
Connection Alias window, on which you can add and enable a connection alias. ?Delete–Removes the selected row from the connection alias table. There is no confirmation or undo. ?Group URLs–Lists in a table the existing group URLs
and their status and lets you add or delete items in that table. A group URL appears on the user login page if the connection is configured to allow users to select a particular group at login. ?Add–Opens the Add Group URL window, on which
you can add and enable a group URL. ?Delete–Removes the selected row from the connection alias table. There is no confirmation or undo.
QUESTION 47
Which functionality is provided by L2TPv3 over FlexVPN?
A. the extension of a Layer 2 domain across the FlexVPNB. the extension of a Layer 3 domain across the FlexVPN
C. secure communication between servers on the FlexVPN
D. a secure backdoor for remote access users through the FlexVPN
Correct Answer: A
Explanation
QUESTION 48
Scenario:
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the Cisco ASA and branch ISR, verify the IPsec configuration is properly
configured between the two sites.
NOTE: the show running-config command cannot be used for this exercise.
Topology: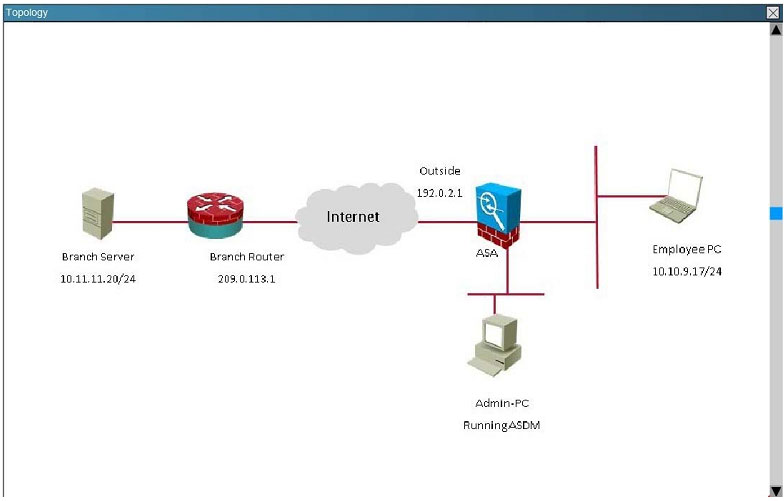


What is being used as the authentication method on the branch ISR?A. Certifcates
B. Pre-shared keys
C. RSA public keys
D. Diffie-Hellman Group 2
Correct Answer: B
Explanation
Explanation/Reference:
The show crypto isakmp key command shows the preshared key of “cisco”. 
QUESTION 49
Scenario:
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the Cisco ASA and branch ISR, verify the IPsec configuration is properly
configured between the two sites.
NOTE: the show running-config command cannot be used for this exercise.
Topology: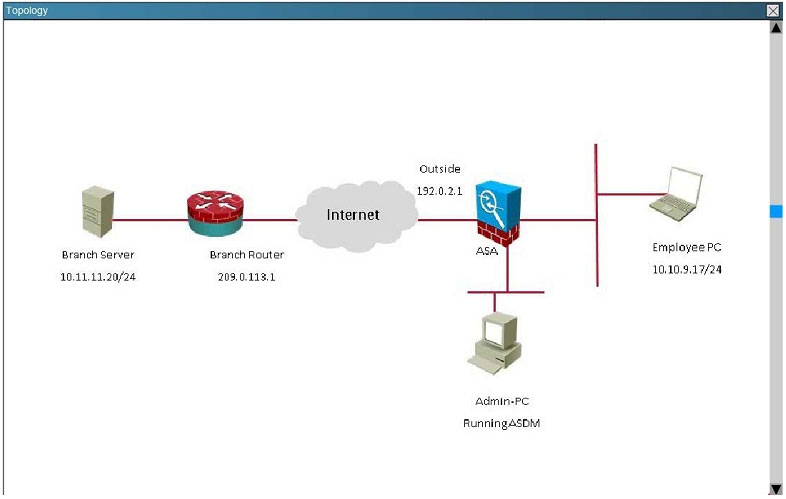


In what state is the IKE security association in on the Cisco ASA?
A. There are no security associations in place
B. MM_ACTIVE
C. ACTIVE(ACTIVE)
D. QM_IDLE
Correct Answer: B
Explanation
Explanation/Reference:
This can be seen from the “show crypto isa sa” command:
QUESTION 50
Scenario:
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the Cisco ASA and branch ISR, verify the IPsec configuration is properly
configured between the two sites.
NOTE: the show running-config command cannot be used for this exercise.
Topology: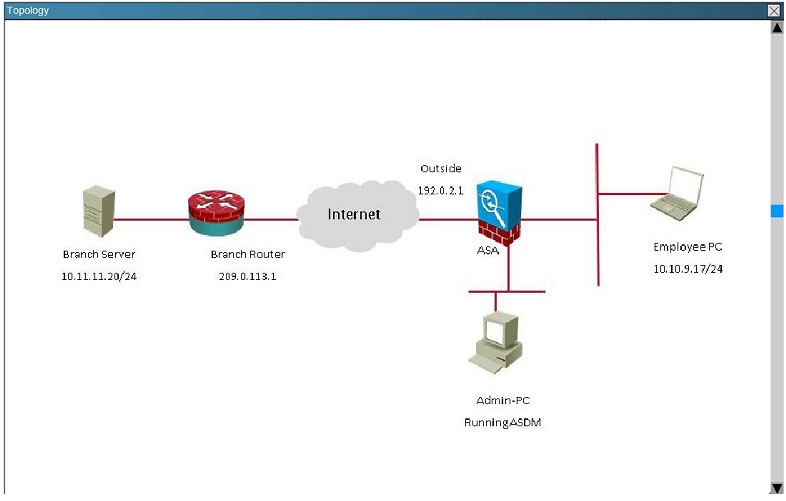


Which crypto map tag is being used on the Cisco ASA?
A. outside_cryptomap
B. VPN-to-ASA
C. L2L_Tunnel
D. outside_map1
Correct Answer: D
Explanation
Explanation/Reference:
This is seen from the “show crypto ipsec sa” command on the ASA.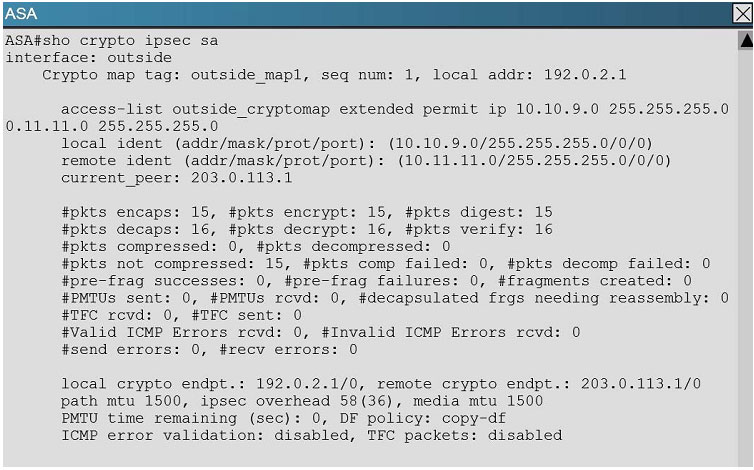
Conclusion:
Congratulations on reading here! Passing the Cisco CCNP Security 300-209 exam is not an easy task, you first need to understand the details of the exam, and then you have to choose a truly valid 300-209 test material (Implementing Cisco Secure Mobility Solutions (SIMOS) v1.0): https://www.geekcert.com/300-209.html (Q&As: 393 PDF + VCE),
finally you need to study hard and get ready for the exam.Choosing geekcert will make your Cisco 300-209 exam very easy.
[PDF] Free Cisco CCNP Security 300-209 dumps download from Google Drive: https://drive.google.com/open?id=1MYSeWmuvxbdVhJPeADLQgrXqZHCC4ua2
[PDF] Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1Qzc3W-UXHXeCJZQZIsYAVUuIacAB5JWN
geekcert Promo Code 15% Off

related: https://www.freecertexam.com/free-cisco-300-101-dumps/
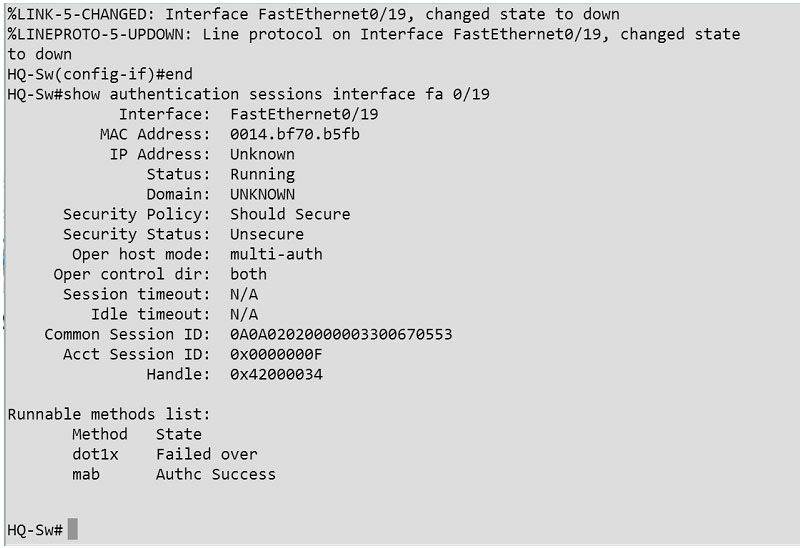
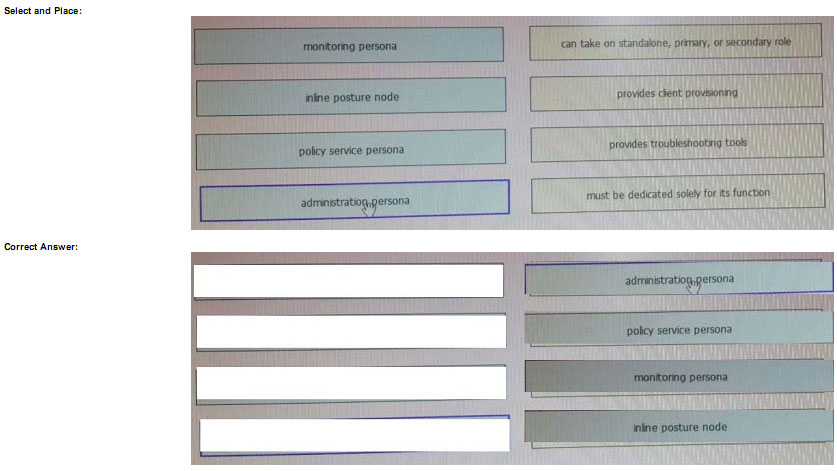
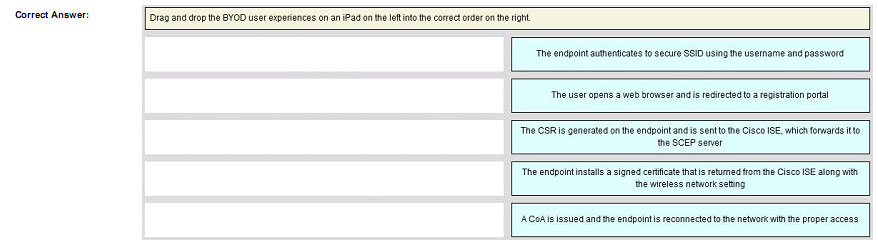
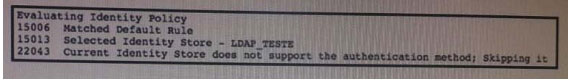 Refer to the exhibit. Which authentication method is being used?
Refer to the exhibit. Which authentication method is being used?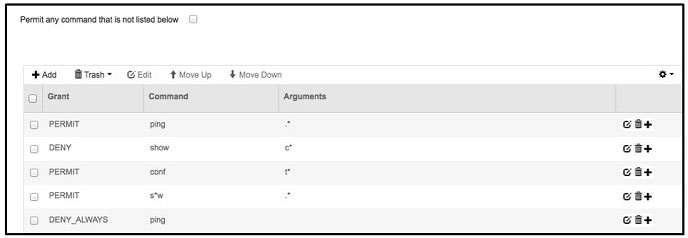 If a user with privilege 15 is matching this command set on Cisco ISE 2.0, which three commands can the user execute? (Choose three.)
If a user with privilege 15 is matching this command set on Cisco ISE 2.0, which three commands can the user execute? (Choose three.)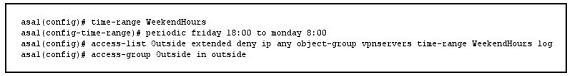 If the given configuration is applied to the object-group vpnservers, during which time period are external users able to connect?
If the given configuration is applied to the object-group vpnservers, during which time period are external users able to connect?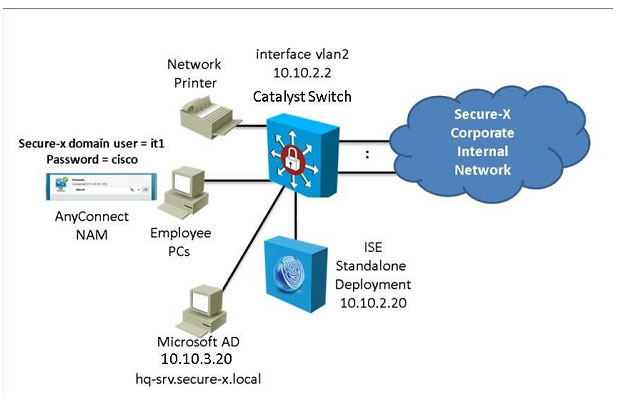 Correct Answer: Review the explanation for full configuration and solution.
Correct Answer: Review the explanation for full configuration and solution.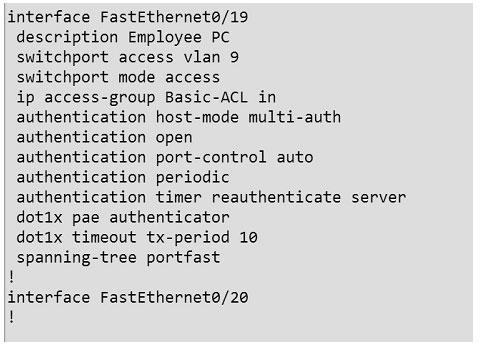
 Explanation
Explanation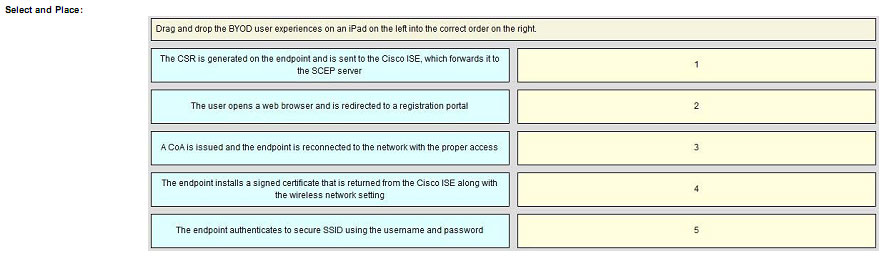
 Explanation
Explanation