

New 312-50V12 Exam Dumps – Practice With Updated Questions And Answers Will Make Things Perfect

Want to make your EC-COUNCIL (CEHv12) 312-50V12 exam perfect? Using the new 312-50V12 exam dumps and taking advantage of the updated questions and answers exercises will make you realize.
Download pass4itsure just updated new 312-50V12 exam dumps (available in both PDF and VCE options) https://www.pass4itsure.com/312-50v12.html and you can be confident that you are preparing updated questions and answers that make your preparation flawless.
pass4itsure provides up-to-date and authentic 312-50V12 mock exam questions and answers for (CEHv12) 512-50V12 exam 528+. These updated questions and answers follow the latest exam guidelines, schedules, and patterns, ensuring that you are learning the most relevant content. Here also provides free 312-50V12 questions and answersfor you to practice.
![(New Arrival) ISC CISSP Questions [Latest] – CISSP Exam Dumps](https://www.freecertexam.com/wp-content/uploads/2024/03/ISC-CISSP-Dumps.png)
(New Arrival) ISC CISSP Questions [Latest] – CISSP Exam Dumps

Hello everyone! Freecertexam Blog, I would like to share the necessary CISSP questions (new) CISSP exam dumps to prepare for the ISC CISSP exam. Let me tell you that pass4itsure has updated ISC CISSP Exam Dumps along with 1703 new ISC CISSP questions that are verified and authentically valid.
You can download the latest CISSP exam dumps https://www.pass4itsure.com/cissp.html Select mode PDF or VCE to get new CISSP exam questions and easily prepare for the Certified Information Systems Security Professional exam.
» Read more about: (New Arrival) ISC CISSP Questions [Latest] – CISSP Exam Dumps »
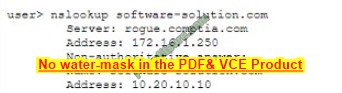
Are CompTIA sy0-601 dumps your must-have practice material?
Yes, this is the best solution!
CompTIA sy0-601 dumps come with both PDF and VCE exercises!
Search data from Google, Youtube, Reddit, and Meta… reveals that a large percentage of candidates are looking for Cisco sy0-601 exam practice materials! their first step through various learning styles
Help them learn the CompTIA sy0-601 exam content by themselves, the second step is to get the latest CompTIA sy0-601 dumps practice materials before the exam to help them easily pass the Cisco sy0-601 certification exam.
» Read more about: Are CompTIA sy0-601 dumps your must-have practice material? »
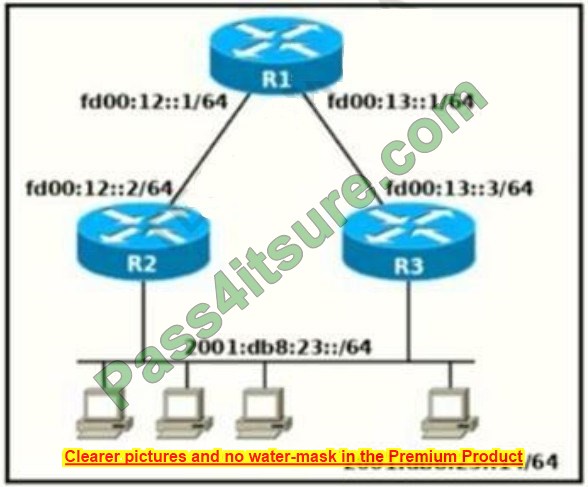
200-301 Dumps Updates And Some Guidelines That Should Be Noted
If you’re looking for a breakthrough point, you want to pass the Cisco CCNA 200-301 exam. My advice to you is:
Get the latest 200-301 dumps and some guidelines to remember.
The latest 200-301 dumps are available at pass4itsure https://www.pass4itsure.com/200-301.html Fresh Questions 1205+ to help you break through the exam.
About the exam 200-301 guidelines, below I will share them one by one, not only that but I also bring you the latest exam questions of pass4itsure 200-301 dumpsonline reading.
» Read more about: 200-301 Dumps Updates And Some Guidelines That Should Be Noted »
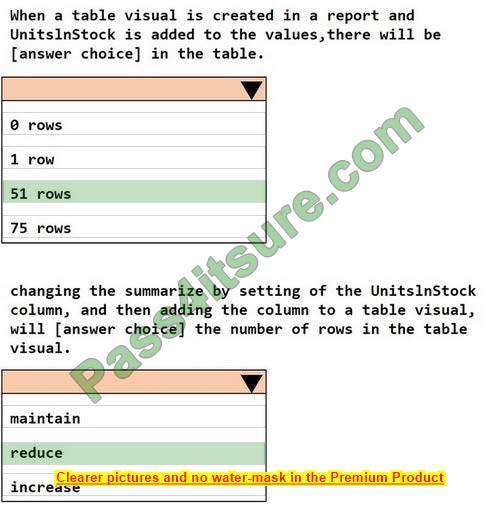
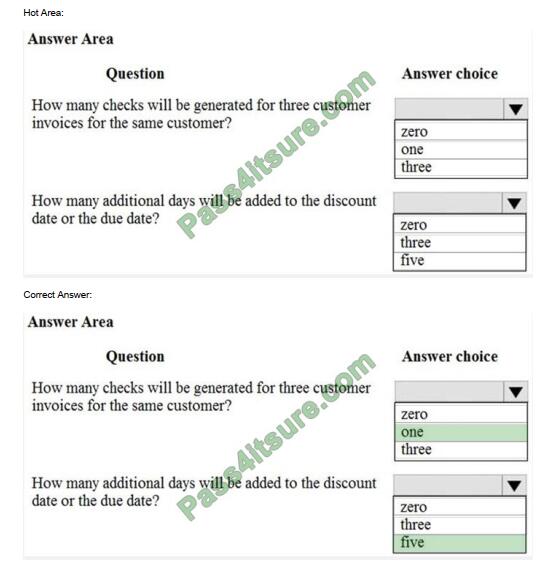
PL-300 Dumps 2023 | Effective Tools To Pass The Exam Successfully

In the Microsoft Power BI Data Analyst exam, are the PL-300 dumps important? Did you encounter the following doubts, and the top three based on voting are as follows:
- Why did the PL-300 knowledge that I saw turn around and forget?
- Are the PL-300 dumps 2023 valid?
- Is it true that practicing the PL-300 exam questions over and over again is valid?
These questions will answer in the Freecertexam blog. But now I want to share practical tools for passing the PL-300 exam. This is important for exams. Our updated PL-300 dumps 2023 https://www.pass4itsure.com/pl-300.html is an effective tool to help you passthe exam.
» Read more about: PL-300 Dumps 2023 | Effective Tools To Pass The Exam Successfully »
MB-310 Exam Dumps Updated | Valid Microsoft Dynamics 365 Finance Exam Practice Material
Microsoft Dynamics 365 Finance exam practice materials are better at helping you prepare for the MB-310 exam. If you need useful Microsoft Dynamics 365 Finance exam practice materials to prepare for the Microsoft MB-310 exam, you can visit our pass4itsure website: https://www.pass4itsure.com/mb-310.html for the latest MB-310 exam dumps as preparation practice materials.
Rest assured, with pass4itsure MB-310 exam dumps, you will win the exam with excellent results.
![DP-900 Dumps [Updated] Valid Microsoft Azure Data Fundamentals Study Questions](https://www.freecertexam.com/wp-content/uploads/2022/08/DP-900-exam-questions-q7-3.jpg)
DP-900 Dumps [Updated] Valid Microsoft Azure Data Fundamentals Study Questions
DP-900 exam study questions are very useful for preparing for the exam. Please note that the DP-900 dumps have been updated with the latest Microsoft Azure Data Fundamentals study questions to effectively help you pass the Microsoft DP-900 exam.
The DP-900 dumps are available online with https://www.pass4itsure.com/dp-900.html 177 real DP-900 study questions to help you take the exam.
Do you have any of these doubts? Microsoft Azure Data Fundamentals exam?
What is the Microsoft DP-900 Exam?
» Read more about: DP-900 Dumps [Updated] Valid Microsoft Azure Data Fundamentals Study Questions »
![1V0-81.20 Dumps [Updated] Correct 1V0-81.20 Preparation Path 010-160 exam questions-q6](https://www.freecertexam.com/wp-content/uploads/2021/01/010-160-exam-questions-q6.jpg)
1V0-81.20 Dumps [Updated] Correct 1V0-81.20 Preparation Path
The correct preparation path is key to passing the VMware 1V0-81.20 exam. If you want to pass the Associate VMware Security exam, 1V0-81.20 dumps will be your preferred resource for preparing for the VMware 1V0-81.20 exam, which is the correct 1V0-81.20 preparation path.
Updated 1V0-81.20 dumps download it: https://www.pass4itsure.com/1v0-81-20.html Get ready for the certification exam!
What do you focus on in the VMware 1V0-81.20 exam?
Exam Full Name: Associate VMware Security
Exam Code: 1V0-81.20
Certification: VCTA-SEC 2021
language: English
Exam time: 120 minutes
Number of questions: 55
Passing Score: VMware exams are scored on a scale of 100-500, with a determined raw score range of 300
Exam Fee: $125
Skill:
- NSX-T Data Center 3.0
- Workspace ONE 20. X
- VMware Carbon Black Cloud
Official study materials:
- VMware Customer Connect Learning
- VMware Press
- VMware Certification Market Place
- VCP Community
Correct Preparation Path: pass4itsure 1V0-81.20 Dumps
How do I prepare for the Associate VMware Security exam effectively?
The following pages provide you with detailed insights to help you effectively prepare for a successful Associate VMware Security exam.
Preparing for the 1V0-81.20 exam requires the correct preparation path, and the 1V0-81.20 dumps is the correct preparation path. In particular, pass4itsure offers. You can rely on the real practice questions in pass4itsure’s
» Read more about: 1V0-81.20 Dumps [Updated] Correct 1V0-81.20 Preparation Path »
500-701 Exam Dumps Latest Version Update Ease Your Success Exam
Cisco exam 500-701 is designed to test your mastery of Cisco Video Infrastructure Design. Did you fail your first Cisco 500-701 exam? If that’s the case, pass4itsure’s Cisco 500-701 exam dumps are a huge help for everyone who passes the 500-701 exam for the first time.
pass4itsure launches the latest Cisco 500-701 exam dumps Mar2022 PDF+VCE https://www.pass4itsure.com/500-701.html (Unique Cisco 500-701 Question 70+) to make it easier for test-takersto navigate the exam with confidence.
» Read more about: 500-701 Exam Dumps Latest Version Update Ease Your Success Exam »
Practice for the Microsoft MS-700 Exam From Pass4itSure
Don’t know how to successfully prepare for the MS-700 exam? No matter what the exam, practice is king. Microsoft Managing Microsoft Team MS-700 is no exception. With the pass4itsure MS-700 exam dumps, don’t worry about it.

Updated MS-700 exam dumps link https://www.pass4itsure.com/ms-700.html Provides the most reliable and trustworthy source for MS-700 questions.
» Read more about: Practice for the Microsoft MS-700 Exam From Pass4itSure »